You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
SOLVED several BSODs on startup
- Thread starter Seko
- Start date
- Joined
- Sep 22, 2010
- Messages
- 613
- Reaction score
- 102
Code:
BugCheck A, {0, 2, 0, fffff800030ed2b3}
IRQL_NOT_LESS_OR_EQUAL (a)
Probably caused by : win32k.sys ( win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+4d )
------------------------
BugCheck D1, {fffff880090f96c0, 2, 0, fffff88001107c50}
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
Probably caused by : ataport.SYS ( ataport!IdeLogCrbActive+bc )
------------------------
BugCheck A, {1, 2, 0, fffff800030ab436}
IRQL_NOT_LESS_OR_EQUAL (a)
Probably caused by : win32k.sys ( win32k!DxLddmCleanupAtProcessDestroy+255 )
------------------------
BugCheck 3B, {c0000005, fffff8000337dc9a, fffff88007be7cb0, 0}
SYSTEM_SERVICE_EXCEPTION (3b)
Probably caused by : ntkrnlmp.exe ( nt!ObpDeleteNameCheck+2a )cybercore said:Your memory is currently set 6-6-6-18-52, while it's meant to be set this way:
DDR400Mhz 6-6-6-18-24 1.80v
1. Set all RAM related settings to 'Auto' - or load optimized defaults in the BIOS.
2. If it's not the right way while set 'Auto' then set it manually DDR400Mhz 6-6-6-18-24 1.80v.
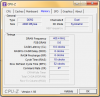
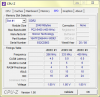
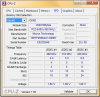
Seiko said:1. I don't find where I can change this in my BIOS, AUTO doesn't change anything.
2. In the SPD tab everything is as you said that it should be
1. Attach your CPU-Z tabs as of now - memory and spd of all slots, not just slot #1
2. Uninstall speedfan. I would hardly supect it but anyway
3. Uninstall Catalyst. Clear up with the Driver Sweeper from Guru3D. Install Catalyst 10.3-10.9
Crash Dumps:
Code:
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\a\Minidump\D M P\DMP\011411-22698-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7600 MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7600.16617.amd64fre.win7_gdr.100618-1621
Machine Name:
Kernel base = 0xfffff800`0305d000 PsLoadedModuleList = 0xfffff800`0329ae50
Debug session time: Fri Jan 14 15:22:01.690 2011 (UTC - 5:00)
System Uptime: 0 days 0:00:30.625
Loading Kernel Symbols
...............................................................
................................................................
...
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {0, 2, 0, fffff800030ed2b3}
Probably caused by : win32k.sys ( win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+4d )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000000000, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff800030ed2b3, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800033050e0
0000000000000000
CURRENT_IRQL: 2
FAULTING_IP:
nt!IopCompleteRequest+ae3
fffff800`030ed2b3 488b09 mov rcx,qword ptr [rcx]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: nvvsvc.exe
IRP_ADDRESS: ffffffffffffff89
TRAP_FRAME: fffff88002b40310 -- (.trap 0xfffff88002b40310)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff88002b403e8 rbx=0000000000000000 rcx=0000000000000000
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff800030ed2b3 rsp=fffff88002b404a0 rbp=fffff88002b405f0
r8=0000000000000000 r9=fffff88002b405a0 r10=0000000000000002
r11=fffffa8005c4f5a0 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz ac po cy
nt!IopCompleteRequest+0xae3:
fffff800`030ed2b3 488b09 mov rcx,qword ptr [rcx] ds:00000000`00000000=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff800030ccca9 to fffff800030cd740
STACK_TEXT:
fffff880`02b401c8 fffff800`030ccca9 : 00000000`0000000a 00000000`00000000 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffff880`02b401d0 fffff800`030cb920 : 00000000`00000001 fffffa80`05ae97b0 fffffa80`05cb7988 fffff800`030d4992 : nt!KiBugCheckDispatch+0x69
fffff880`02b40310 fffff800`030ed2b3 : 00000000`00000000 fffff800`030e77c0 fffffa80`05cc5100 00000000`00000000 : nt!KiPageFault+0x260
fffff880`02b404a0 fffff800`030aa0c7 : 00000000`00000001 fffff960`001a43a9 fffff900`c0207a00 fffff800`00000000 : nt!IopCompleteRequest+0xae3
fffff880`02b40570 fffff800`030aa487 : 00000000`00008988 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDeliverApc+0x1d7
fffff880`02b405f0 fffff960`001add49 : 00000000`0105051b 00000000`00000000 00000000`00000000 00000000`00000528 : nt!KiApcInterrupt+0xd7
fffff880`02b40780 fffff960`001ad7d5 : 00000000`00000000 fffff880`02b40b1f 00000000`00000528 00000000`00000000 : win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+0x4d
fffff880`02b407b0 fffff960`001a4c00 : 00000000`00000528 fffff880`02b40b00 fffff900`c1d60ce0 fffff900`00000000 : win32k!NtGdiCloseProcess+0x441
fffff880`02b40810 fffff960`001a4337 : fffffa80`055a2900 fffff880`02b40be0 00020508`00000000 00000000`00000701 : win32k!GdiProcessCallout+0x200
fffff880`02b40890 fffff800`033b2a01 : fffffa80`055a2960 00000000`00000000 00000000`00000000 fffffa80`05cc5060 : win32k!W32pProcessCallout+0x6b
fffff880`02b408c0 fffff800`0338b635 : 00000000`00000000 fffff800`033cc101 fffffa80`78457300 00000000`00000000 : nt!PspExitThread+0x561
fffff880`02b40980 fffff800`030aa1db : fffffa80`05c9a601 fffffa80`058a8850 00000000`00000000 00000000`00000000 : nt!PsExitSpecialApc+0x1d
fffff880`02b409b0 fffff800`030aa620 : 00000000`00371290 fffff880`02b40a30 fffff800`0338b74c 00000000`00000001 : nt!KiDeliverApc+0x2eb
fffff880`02b40a30 fffff800`030cca37 : fffffa80`05c7d490 00000000`00000001 fffffa80`05cc5060 fffff800`033e3414 : nt!KiInitiateUserApc+0x70
fffff880`02b40b70 00000000`7721008a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9c
00000000`0116f508 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7721008a
STACK_COMMAND: kb
FOLLOWUP_IP:
win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+4d
fffff960`001add49 413ac4 cmp al,r12b
SYMBOL_STACK_INDEX: 6
SYMBOL_NAME: win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+4d
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: win32k
IMAGE_NAME: win32k.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4cbe5d3e
FAILURE_BUCKET_ID: X64_0xA_win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+4d
BUCKET_ID: X64_0xA_win32k!MultiUserGreCleanupHmgOwnRemoveAllLocks+4d
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\a\Minidump\D M P\DMP\011411-23150-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7600 MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7600.16617.amd64fre.win7_gdr.100618-1621
Machine Name:
Kernel base = 0xfffff800`03053000 PsLoadedModuleList = 0xfffff800`03290e50
Debug session time: Fri Jan 14 15:20:33.716 2011 (UTC - 5:00)
System Uptime: 0 days 8:00:58.651
Loading Kernel Symbols
...............................................................
................................................................
................
Loading User Symbols
Loading unloaded module list
.....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck D1, {fffff880090f96c0, 2, 0, fffff88001107c50}
Probably caused by : ataport.SYS ( ataport!IdeLogCrbActive+bc )
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If kernel debugger is available get stack backtrace.
Arguments:
Arg1: fffff880090f96c0, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, value 0 = read operation, 1 = write operation
Arg4: fffff88001107c50, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800032fb0e0
fffff880090f96c0
CURRENT_IRQL: 2
FAULTING_IP:
ataport!IdeLogCrbActive+bc
fffff880`01107c50 f30f6f4148 movdqu xmm0,xmmword ptr [rcx+48h]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xD1
PROCESS_NAME: iw4mp.dat
TRAP_FRAME: fffff880009b06e0 -- (.trap 0xfffff880009b06e0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffffa80038c67e0 rbx=0000000000000000 rcx=fffff880090f9670
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff88001107c50 rsp=fffff880009b0870 rbp=0000000000000001
r8=0000000000000000 r9=0000000000000000 r10=fffffa80043b6be0
r11=fffff880009b09a0 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na pe nc
ataport!IdeLogCrbActive+0xbc:
fffff880`01107c50 f30f6f4148 movdqu xmm0,xmmword ptr [rcx+48h] ds:8120:fffff880`090f96b8=????????????????????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff800030c2ca9 to fffff800030c3740
STACK_TEXT:
fffff880`009b0598 fffff800`030c2ca9 : 00000000`0000000a fffff880`090f96c0 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffff880`009b05a0 fffff800`030c1920 : fffff880`02f63180 fffffa80`044db1d0 00000000`00000000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
fffff880`009b06e0 fffff880`01107c50 : 3fe00000`00000000 3fe00000`00000000 fffffa80`044d91b0 00000000`00000001 : nt!KiPageFault+0x260
fffff880`009b0870 fffff880`01111c71 : fffffa80`03f90c68 fffffa80`041701a0 fffffa80`03f90b80 bc7b5cee`5c4e4628 : ataport!IdeLogCrbActive+0xbc
fffff880`009b08a0 fffff800`0300e9ce : fffffa80`03f90c68 00000000`00000018 00000000`00000000 00000000`00000001 : ataport!IdeStartIoCallBack+0xc9
fffff880`009b0a10 fffff800`0300f13d : fffffa80`041525b0 fffffa80`043a9e70 fffffa80`043a9e00 00000000`00000000 : hal!HalpAllocateAdapterCallback+0x146
fffff880`009b0ab0 fffff800`0300e71f : fffffa80`03f90c20 00000000`00000200 fffffa80`043a9e70 fffffa80`058cd010 : hal!HalAllocateAdapterChannel+0x101
fffff880`009b0af0 fffff880`010d40d3 : fffffa80`03f90b80 fffff880`010d412c fffffa80`000000a0 fffffa80`043a9e70 : hal!HalBuildScatterGatherList+0x2f3
fffff880`009b0b60 fffff880`01111b3b : fffffa80`03f90b80 fffffa80`044d91b0 fffffa80`041701a0 fffffa80`03f90b80 : PCIIDEX!BmSetup+0x6b
fffff880`009b0bc0 fffff880`011107eb : fffffa80`04171500 fffffa80`044d91b0 fffffa80`04171500 fffffa80`041701a0 : ataport!IdeDispatchChannelRequest+0xef
fffff880`009b0bf0 fffff880`0111031e : 00000000`00000001 fffffa80`03f90b80 00000000`00000001 fffffa80`03f90b80 : ataport!IdeStartChannelRequest+0x113
fffff880`009b0c70 fffff880`01112582 : fffffa80`04e14668 00000000`00000000 fffffa80`044d91b0 fffffa80`0624eb00 : ataport!IdeStartNextDeviceRequest+0x18e
fffff880`009b0d10 fffff880`011120ec : fffffa80`041701a0 00000000`00000000 fffffa80`041701a0 fffffa80`0624eb00 : ataport!IdeProcessCompletedRequests+0x26a
fffff880`009b0e40 fffff800`030cebfc : fffff880`02fd3180 fffffa80`001c3a2d fffffa80`04170050 fffffa80`04170118 : ataport!IdePortCompletionDpc+0x1a8
fffff880`009b0f00 fffff800`030c9865 : 33003800`38003000 fffffa80`04cb7b00 00000000`00000000 fffff880`01111f44 : nt!KiRetireDpcList+0x1bc
fffff880`009b0fb0 fffff800`030c967c : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KxRetireDpcList+0x5
fffff880`02e82ba0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDispatchInterruptContinue
STACK_COMMAND: kb
FOLLOWUP_IP:
ataport!IdeLogCrbActive+bc
fffff880`01107c50 f30f6f4148 movdqu xmm0,xmmword ptr [rcx+48h]
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: ataport!IdeLogCrbActive+bc
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: ataport
IMAGE_NAME: ataport.SYS
DEBUG_FLR_IMAGE_TIMESTAMP: 4a5bc118
FAILURE_BUCKET_ID: X64_0xD1_ataport!IdeLogCrbActive+bc
BUCKET_ID: X64_0xD1_ataport!IdeLogCrbActive+bc
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\a\Minidump\D M P\DMP\011411-36036-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7600 MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7600.16617.amd64fre.win7_gdr.100618-1621
Machine Name:
Kernel base = 0xfffff800`0301b000 PsLoadedModuleList = 0xfffff800`03258e50
Debug session time: Fri Jan 14 07:18:43.729 2011 (UTC - 5:00)
System Uptime: 0 days 0:02:49.664
Loading Kernel Symbols
...............................................................
................................................................
................
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {1, 2, 0, fffff800030ab436}
Probably caused by : win32k.sys ( win32k!DxLddmCleanupAtProcessDestroy+255 )
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000000001, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff800030ab436, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800032c30e0
0000000000000001
CURRENT_IRQL: 2
FAULTING_IP:
nt!IopCompleteRequest+c73
fffff800`030ab436 488b09 mov rcx,qword ptr [rcx]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: AtBroker.exe
IRP_ADDRESS: ffffffffffffff88
TRAP_FRAME: fffff88003806280 -- (.trap 0xfffff88003806280)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff880038063e8 rbx=0000000000000000 rcx=0000000000000001
rdx=0000000000000001 rsi=0000000000000000 rdi=0000000000000000
rip=fffff800030ab436 rsp=fffff88003806410 rbp=fffff88003806560
r8=fffffa80061f25b0 r9=fffff88003806510 r10=0000000000000002
r11=fffffa80050d5810 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz ac pe cy
nt!IopCompleteRequest+0xc73:
fffff800`030ab436 488b09 mov rcx,qword ptr [rcx] ds:0010:00000000`00000001=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff8000308aca9 to fffff8000308b740
STACK_TEXT:
fffff880`03806138 fffff800`0308aca9 : 00000000`0000000a 00000000`00000001 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffff880`03806140 fffff800`03089920 : 00000014`00000000 fffffa80`04de3380 fffffa80`04de3380 fffff880`00e107b3 : nt!KiBugCheckDispatch+0x69
fffff880`03806280 fffff800`030ab436 : fffffa80`058a3c50 fffff880`0508d49e 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x260
fffff880`03806410 fffff800`030680c7 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!IopCompleteRequest+0xc73
fffff880`038064e0 fffff800`03068487 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDeliverApc+0x1d7
fffff880`03806560 fffff800`03097792 : fffff900`c00c0020 00000000`00000000 00000000`00000000 00000000`00000bdc : nt!KiApcInterrupt+0xd7
fffff880`038066f0 fffff960`0025af51 : fffff900`c00bf010 fffff900`c00bf010 00000000`00000000 00000000`00000bdc : nt!ExReleaseResourceAndLeaveCriticalRegion+0x32
fffff880`03806720 fffff960`0019d52e : 00000000`00000000 fffff880`03806b1f 00000000`00000bdc fffff900`c065dce0 : win32k!DxLddmCleanupAtProcessDestroy+0x255
fffff880`038067b0 fffff960`00194c00 : 00000000`00000bdc fffff880`03806b00 fffff900`c065dce0 fffff900`00000000 : win32k!NtGdiCloseProcess+0x19a
fffff880`03806810 fffff960`00194337 : fffffa80`0598aa00 fffff880`03806be0 00020508`00000000 fffff8a0`001cc001 : win32k!GdiProcessCallout+0x200
fffff880`03806890 fffff800`03370a01 : fffffa80`0598aa60 00000000`00000000 00000000`00000000 fffffa80`05259950 : win32k!W32pProcessCallout+0x6b
fffff880`038068c0 fffff800`03349635 : 00000000`00000001 fffff800`0338a101 fffffa80`78457300 00000000`00000000 : nt!PspExitThread+0x561
fffff880`03806980 fffff800`030681db : fffffa80`05936001 fffffa80`063e1010 00000000`00000000 00000000`00000000 : nt!PsExitSpecialApc+0x1d
fffff880`038069b0 fffff800`03068620 : 00000000`001f8a60 fffff880`03806a30 fffff800`0334974c 00000000`00000001 : nt!KiDeliverApc+0x2eb
fffff880`03806a30 fffff800`0308aa37 : 00000000`00000323 fffff8a0`00000000 00000000`00000001 0000007f`ffffffff : nt!KiInitiateUserApc+0x70
fffff880`03806b70 00000000`7750008a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9c
00000000`01e0ed58 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7750008a
STACK_COMMAND: kb
FOLLOWUP_IP:
win32k!DxLddmCleanupAtProcessDestroy+255
fffff960`0025af51 ff1541651100 call qword ptr [win32k!_imp_PsLeavePriorityRegion (fffff960`00371498)]
SYMBOL_STACK_INDEX: 7
SYMBOL_NAME: win32k!DxLddmCleanupAtProcessDestroy+255
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: win32k
IMAGE_NAME: win32k.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4cbe5d3e
FAILURE_BUCKET_ID: X64_0xA_win32k!DxLddmCleanupAtProcessDestroy+255
BUCKET_ID: X64_0xA_win32k!DxLddmCleanupAtProcessDestroy+255
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\a\Minidump\D M P\DMP\011411-36941-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7600 MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7600.16617.amd64fre.win7_gdr.100618-1621
Machine Name:
Kernel base = 0xfffff800`03011000 PsLoadedModuleList = 0xfffff800`0324ee50
Debug session time: Fri Jan 14 07:12:39.012 2011 (UTC - 5:00)
System Uptime: 0 days 0:02:10.557
Loading Kernel Symbols
...............................................................
................................................................
................
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 3B, {c0000005, fffff8000337dc9a, fffff88007be7cb0, 0}
Probably caused by : ntkrnlmp.exe ( nt!ObpDeleteNameCheck+2a )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: fffff8000337dc9a, Address of the instruction which caused the bugcheck
Arg3: fffff88007be7cb0, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
FAULTING_IP:
nt!ObpDeleteNameCheck+2a
fffff800`0337dc9a f0480fba691000 lock bts qword ptr [rcx+10h],0
CONTEXT: fffff88007be7cb0 -- (.cxr 0xfffff88007be7cb0)
rax=fffffa800386bb60 rbx=0000000000000000 rcx=0000000104d3bb30
rdx=fffffa80061e0931 rsi=0000000104d3bb30 rdi=0000000000000200
rip=fffff8000337dc9a rsp=fffff88007be8680 rbp=0050a00000000000
r8=fffffa80061e0930 r9=fffff880009ea180 r10=fffffa8003745f00
r11=fffffa800634c010 r12=fffffa8000000000 r13=0000000000000001
r14=fffffa80050bb400 r15=fffff8a002b6dc70
iopl=0 nv up ei ng nz ac po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010296
nt!ObpDeleteNameCheck+0x2a:
fffff800`0337dc9a f0480fba691000 lock bts qword ptr [rcx+10h],0 ds:002b:00000001`04d3bb40=????????????????
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x3B
PROCESS_NAME: hkcmd.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from 0000000000000000 to fffff8000337dc9a
STACK_TEXT:
fffff880`07be8680 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!ObpDeleteNameCheck+0x2a
FOLLOWUP_IP:
nt!ObpDeleteNameCheck+2a
fffff800`0337dc9a f0480fba691000 lock bts qword ptr [rcx+10h],0
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: nt!ObpDeleteNameCheck+2a
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 4c1c44a9
STACK_COMMAND: .cxr 0xfffff88007be7cb0 ; kb
FAILURE_BUCKET_ID: X64_0x3B_nt!ObpDeleteNameCheck+2a
BUCKET_ID: X64_0x3B_nt!ObpDeleteNameCheck+2a
Followup: MachineOwner
---------Drivers:
Code:
start end module name
fffff880`00ed1000 fffff880`00f28000 ACPI ACPI.sys Mon Jul 13 19:19:34 2009 (4A5BC106)
fffff880`02c77000 fffff880`02d01000 afd afd.sys Mon Jul 13 19:21:40 2009 (4A5BC184)
fffff880`03b68000 fffff880`03b7e000 AgileVpn AgileVpn.sys Mon Jul 13 20:10:24 2009 (4A5BCCF0)
fffff880`010f3000 fffff880`010fe000 amdxata amdxata.sys Tue May 19 13:56:59 2009 (4A12F2EB)
fffff880`051f6000 fffff880`051fe000 ASACPI ASACPI.sys Wed Jul 15 23:31:29 2009 (4A5E9F11)
fffff880`019d5000 fffff880`019db000 AsIO AsIO.sys Mon Aug 03 03:03:16 2009 (4A768BB4)
fffff880`02c6e000 fffff880`02c74000 AsUpIO AsUpIO.sys Sun Jul 05 22:21:38 2009 (4A515FB2)
fffff880`00fd7000 fffff880`00fe0000 atapi atapi.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`010c9000 fffff880`010f3000 ataport ataport.SYS Mon Jul 13 19:19:52 2009 (4A5BC118)
fffff880`04803000 fffff880`05014000 atikmdag atikmdag.sys Thu Nov 25 21:46:44 2010 (4CEF1F94)
fffff880`03a60000 fffff880`03aac000 atikmpag atikmpag.sys Thu Nov 25 21:16:47 2010 (4CEF188F)
fffff880`01836000 fffff880`0183d000 Beep Beep.SYS Mon Jul 13 20:00:13 2009 (4A5BCA8D)
fffff880`018e2000 fffff880`018f3000 blbdrive blbdrive.sys Mon Jul 13 19:35:59 2009 (4A5BC4DF)
fffff960`007c0000 fffff960`007e7000 cdd cdd.dll Tue Nov 02 00:59:22 2010 (4CCF9AAA)
fffff880`019ab000 fffff880`019d5000 cdrom cdrom.sys Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`00d36000 fffff880`00df6000 CI CI.dll Mon Jul 13 21:32:13 2009 (4A5BE01D)
fffff880`01945000 fffff880`01975000 CLASSPNP CLASSPNP.SYS Mon Jul 13 19:19:58 2009 (4A5BC11E)
fffff880`00cd8000 fffff880`00d36000 CLFS CLFS.SYS Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`01000000 fffff880`01073000 cng cng.sys Mon Jul 13 19:49:40 2009 (4A5BC814)
fffff880`03b58000 fffff880`03b68000 CompositeBus CompositeBus.sys Mon Jul 13 20:00:33 2009 (4A5BCAA1)
fffff880`05e28000 fffff880`05e36000 crashdmp crashdmp.sys Mon Jul 13 20:01:01 2009 (4A5BCABD)
fffff880`02ddf000 fffff880`02dfd000 dfsc dfsc.sys Mon Jul 13 19:23:44 2009 (4A5BC200)
fffff880`02dd0000 fffff880`02ddf000 discache discache.sys Mon Jul 13 19:37:18 2009 (4A5BC52E)
fffff880`0192f000 fffff880`01945000 disk disk.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`05e00000 fffff880`05e22000 drmk drmk.sys Mon Jul 13 21:01:25 2009 (4A5BD8E5)
fffff880`03dbc000 fffff880`03dc5000 dump_atapi dump_atapi.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`03db0000 fffff880`03dbc000 dump_dumpata dump_dumpata.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`03dc5000 fffff880`03dd8000 dump_dumpfve dump_dumpfve.sys Mon Jul 13 19:21:51 2009 (4A5BC18F)
fffff880`02c68000 fffff880`02c6e000 dvdfabio dvdfabio.sys Tue Dec 07 00:19:28 2010 (4CFDC3E0)
fffff880`03dd8000 fffff880`03de4000 Dxapi Dxapi.sys Mon Jul 13 19:38:28 2009 (4A5BC574)
fffff880`05014000 fffff880`05108000 dxgkrnl dxgkrnl.sys Mon Nov 01 22:51:31 2010 (4CCF7CB3)
fffff880`05108000 fffff880`0514e000 dxgmms1 dxgmms1.sys Mon Nov 01 22:50:56 2010 (4CCF7C90)
fffff880`0114a000 fffff880`0115e000 fileinfo fileinfo.sys Mon Jul 13 19:34:25 2009 (4A5BC481)
fffff880`010fe000 fffff880`0114a000 fltmgr fltmgr.sys Mon Jul 13 19:19:59 2009 (4A5BC11F)
fffff880`013f6000 fffff880`01400000 Fs_Rec Fs_Rec.sys Mon Jul 13 19:19:45 2009 (4A5BC111)
fffff880`018f5000 fffff880`0192f000 fvevol fvevol.sys Fri Sep 25 22:34:26 2009 (4ABD7DB2)
fffff880`015a2000 fffff880`015ec000 fwpkclnt fwpkclnt.sys Mon Jul 13 19:21:08 2009 (4A5BC164)
fffff880`01200000 fffff880`01214000 gagp30kx gagp30kx.sys Mon Jul 13 19:38:43 2009 (4A5BC583)
fffff800`03014000 fffff800`0305d000 hal hal.dll Mon Jul 13 21:27:36 2009 (4A5BDF08)
fffff880`0514e000 fffff880`05172000 HDAudBus HDAudBus.sys Mon Jul 13 20:06:13 2009 (4A5BCBF5)
fffff880`03c00000 fffff880`03c19000 HIDCLASS HIDCLASS.SYS Mon Jul 13 20:06:21 2009 (4A5BCBFD)
fffff880`03c19000 fffff880`03c21080 HIDPARSE HIDPARSE.SYS Mon Jul 13 20:06:17 2009 (4A5BCBF9)
fffff880`03de4000 fffff880`03df2000 hidusb hidusb.sys Mon Jul 13 20:06:22 2009 (4A5BCBFE)
fffff880`01412000 fffff880`0141b000 hwpolicy hwpolicy.sys Mon Jul 13 19:19:22 2009 (4A5BC0FA)
fffff880`03b2b000 fffff880`03b49000 i8042prt i8042prt.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`00fa5000 fffff880`00fad000 intelide intelide.sys Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`03a4a000 fffff880`03a60000 intelppm intelppm.sys Mon Jul 13 19:19:25 2009 (4A5BC0FD)
fffff880`03b49000 fffff880`03b58000 kbdclass kbdclass.sys Mon Jul 13 19:19:50 2009 (4A5BC116)
fffff800`00bb5000 fffff800`00bb8000 kdcom kdcom.dll Tue Nov 30 09:40:39 2010 (4CF50CE7)
fffff880`03caf000 fffff880`03cf2000 ks ks.sys Wed Mar 03 23:32:25 2010 (4B8F37D9)
fffff880`013cb000 fffff880`013e5000 ksecdd ksecdd.sys Mon Jul 13 19:20:54 2009 (4A5BC156)
fffff880`01577000 fffff880`015a2000 ksecpkg ksecpkg.sys Fri Dec 11 01:03:32 2009 (4B21E0B4)
fffff880`05e22000 fffff880`05e27200 ksthunk ksthunk.sys Mon Jul 13 20:00:19 2009 (4A5BCA93)
fffff880`03c60000 fffff880`03c75000 lltdio lltdio.sys Mon Jul 13 20:08:50 2009 (4A5BCC92)
fffff880`03c3d000 fffff880`03c60000 luafv luafv.sys Mon Jul 13 19:26:13 2009 (4A5BC295)
fffff880`00c80000 fffff880`00cc4000 mcupdate_GenuineIntel mcupdate_GenuineIntel.dll Mon Jul 13 21:29:10 2009 (4A5BDF66)
fffff880`03c2f000 fffff880`03c3d000 monitor monitor.sys Mon Jul 13 19:38:52 2009 (4A5BC58C)
fffff880`01214000 fffff880`01223000 mouclass mouclass.sys Mon Jul 13 19:19:50 2009 (4A5BC116)
fffff880`03c22000 fffff880`03c2f000 mouhid mouhid.sys Mon Jul 13 20:00:20 2009 (4A5BCA94)
fffff880`00fbd000 fffff880`00fd7000 mountmgr mountmgr.sys Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`01800000 fffff880`0182d000 MpFilter MpFilter.sys Sat Mar 20 01:58:08 2010 (4BA463F0)
fffff880`0189b000 fffff880`018a6000 Msfs Msfs.SYS Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`00f31000 fffff880`00f3b000 msisadrv msisadrv.sys Mon Jul 13 19:19:26 2009 (4A5BC0FE)
fffff880`0115e000 fffff880`011bc000 msrpc msrpc.sys Mon Jul 13 19:21:32 2009 (4A5BC17C)
fffff880`02c5d000 fffff880`02c68000 mssmbios mssmbios.sys Mon Jul 13 19:31:10 2009 (4A5BC3BE)
fffff880`01400000 fffff880`01412000 mup mup.sys Mon Jul 13 19:23:45 2009 (4A5BC201)
fffff880`01425000 fffff880`01517000 ndis ndis.sys Mon Jul 13 19:21:40 2009 (4A5BC184)
fffff880`03ba2000 fffff880`03bae000 ndistapi ndistapi.sys Mon Jul 13 20:10:00 2009 (4A5BCCD8)
fffff880`03bae000 fffff880`03bdd000 ndiswan ndiswan.sys Mon Jul 13 20:10:11 2009 (4A5BCCE3)
fffff880`03d5e000 fffff880`03d73000 NDProxy NDProxy.SYS Mon Jul 13 20:10:05 2009 (4A5BCCDD)
fffff880`02d75000 fffff880`02d84000 netbios netbios.sys Mon Jul 13 20:09:26 2009 (4A5BCCB6)
fffff880`02d01000 fffff880`02d46000 netbt netbt.sys Mon Jul 13 19:21:28 2009 (4A5BC178)
fffff880`01517000 fffff880`01577000 NETIO NETIO.SYS Mon Jul 13 19:21:46 2009 (4A5BC18A)
fffff880`018a6000 fffff880`018b7000 Npfs Npfs.SYS Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`02c51000 fffff880`02c5d000 nsiproxy nsiproxy.sys Mon Jul 13 19:21:02 2009 (4A5BC15E)
fffff800`0305d000 fffff800`03639000 nt ntkrnlmp.exe Sat Jun 19 00:16:41 2010 (4C1C44A9)
fffff880`01228000 fffff880`013cb000 Ntfs Ntfs.sys Mon Jul 13 19:20:47 2009 (4A5BC14F)
fffff880`0182d000 fffff880`01836000 Null Null.SYS Mon Jul 13 19:19:37 2009 (4A5BC109)
fffff880`02d4f000 fffff880`02d75000 pacer pacer.sys Mon Jul 13 20:09:41 2009 (4A5BCCC5)
fffff880`03b02000 fffff880`03b1f000 parport parport.sys Mon Jul 13 20:00:40 2009 (4A5BCAA8)
fffff880`00f7b000 fffff880`00f90000 partmgr partmgr.sys Mon Jul 13 19:19:58 2009 (4A5BC11E)
fffff880`00f48000 fffff880`00f7b000 pci pci.sys Mon Jul 13 19:19:51 2009 (4A5BC117)
fffff880`00fad000 fffff880`00fbd000 PCIIDEX PCIIDEX.SYS Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`013e5000 fffff880`013f6000 pcw pcw.sys Mon Jul 13 19:19:27 2009 (4A5BC0FF)
fffff880`03d73000 fffff880`03db0000 portcls portcls.sys Mon Jul 13 20:06:27 2009 (4A5BCC03)
fffff880`00cc4000 fffff880`00cd8000 PSHED PSHED.dll Mon Jul 13 21:32:23 2009 (4A5BE027)
fffff880`03b7e000 fffff880`03ba2000 rasl2tp rasl2tp.sys Mon Jul 13 20:10:11 2009 (4A5BCCE3)
fffff880`03bdd000 fffff880`03bf8000 raspppoe raspppoe.sys Mon Jul 13 20:10:17 2009 (4A5BCCE9)
fffff880`03a00000 fffff880`03a21000 raspptp raspptp.sys Mon Jul 13 20:10:18 2009 (4A5BCCEA)
fffff880`019db000 fffff880`019f5000 rassstp rassstp.sys Mon Jul 13 20:10:25 2009 (4A5BCCF1)
fffff880`02c00000 fffff880`02c51000 rdbss rdbss.sys Mon Jul 13 19:24:09 2009 (4A5BC219)
fffff880`01880000 fffff880`01889000 RDPCDD RDPCDD.sys Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`01889000 fffff880`01892000 rdpencdd rdpencdd.sys Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`01892000 fffff880`0189b000 rdprefmp rdprefmp.sys Mon Jul 13 20:16:35 2009 (4A5BCE63)
fffff880`011bc000 fffff880`011f6000 rdyboost rdyboost.sys Mon Jul 13 19:34:34 2009 (4A5BC48A)
fffff880`00e00000 fffff880`00e18000 rspndr rspndr.sys Mon Jul 13 20:08:50 2009 (4A5BCC92)
fffff880`05172000 fffff880`051d8000 Rt64win7 Rt64win7.sys Tue Nov 30 01:01:28 2010 (4CF49338)
fffff880`03c7e000 fffff880`03cad000 SCSIPORT SCSIPORT.SYS Mon Jul 13 20:01:04 2009 (4A5BCAC0)
fffff880`03b1f000 fffff880`03b2b000 serenum serenum.sys Mon Jul 13 20:00:33 2009 (4A5BCAA1)
fffff880`02d84000 fffff880`02da1000 serial serial.sys Mon Jul 13 20:00:40 2009 (4A5BCAA8)
fffff880`015f4000 fffff880`015fb000 speedfan speedfan.sys Sun Sep 24 09:26:48 2006 (45168798)
fffff880`015ec000 fffff880`015f4000 spldr spldr.sys Mon May 11 12:56:27 2009 (4A0858BB)
fffff880`03cad000 fffff880`03cae480 swenum swenum.sys Mon Jul 13 20:00:18 2009 (4A5BCA92)
fffff880`01600000 fffff880`017fd000 tcpip tcpip.sys Sun Jun 13 23:39:04 2010 (4C15A458)
fffff880`018d5000 fffff880`018e2000 TDI TDI.SYS Mon Jul 13 19:21:18 2009 (4A5BC16E)
fffff880`018b7000 fffff880`018d5000 tdx tdx.sys Mon Jul 13 19:21:15 2009 (4A5BC16B)
fffff880`02dbc000 fffff880`02dd0000 termdd termdd.sys Mon Jul 13 20:16:36 2009 (4A5BCE64)
fffff960`00450000 fffff960`0045a000 TSDDD TSDDD.dll unavailable (00000000)
fffff880`03a24000 fffff880`03a4a000 tunnel tunnel.sys Mon Jul 13 20:09:37 2009 (4A5BCCC1)
fffff880`03cf2000 fffff880`03d04000 umbus umbus.sys Mon Jul 13 20:06:56 2009 (4A5BCC20)
fffff880`05e36000 fffff880`05e37f00 USBD USBD.SYS Mon Jul 13 20:06:23 2009 (4A5BCBFF)
fffff880`051e5000 fffff880`051f6000 usbehci usbehci.sys Mon Jul 13 20:06:30 2009 (4A5BCC06)
fffff880`03d04000 fffff880`03d5e000 usbhub usbhub.sys Mon Jul 13 20:07:09 2009 (4A5BCC2D)
fffff880`03aac000 fffff880`03b02000 USBPORT USBPORT.SYS Mon Jul 13 20:06:31 2009 (4A5BCC07)
fffff880`051d8000 fffff880`051e5000 usbuhci usbuhci.sys Mon Jul 13 20:06:27 2009 (4A5BCC03)
fffff880`00fe0000 fffff880`00fee000 vdrive vdrive.sys Tue Dec 07 00:19:28 2010 (4CFDC3E0)
fffff880`00f3b000 fffff880`00f48000 vdrvroot vdrvroot.sys Mon Jul 13 20:01:31 2009 (4A5BCADB)
fffff880`0183d000 fffff880`0184b000 vga vga.sys Mon Jul 13 19:38:47 2009 (4A5BC587)
fffff880`05e38000 fffff880`05ff9000 viahduaa viahduaa.sys Wed Aug 04 03:51:53 2010 (4C591C19)
fffff880`0184b000 fffff880`01870000 VIDEOPRT VIDEOPRT.SYS Mon Jul 13 19:38:51 2009 (4A5BC58B)
fffff880`00f90000 fffff880`00fa5000 volmgr volmgr.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`00c00000 fffff880`00c5c000 volmgrx volmgrx.sys Mon Jul 13 19:20:33 2009 (4A5BC141)
fffff880`01073000 fffff880`010bf000 volsnap volsnap.sys Mon Jul 13 19:20:08 2009 (4A5BC128)
fffff880`02da1000 fffff880`02dbc000 wanarp wanarp.sys Mon Jul 13 20:10:21 2009 (4A5BCCED)
fffff880`01870000 fffff880`01880000 watchdog watchdog.sys Mon Jul 13 19:37:35 2009 (4A5BC53F)
fffff880`00e1e000 fffff880`00ec2000 Wdf01000 Wdf01000.sys Mon Jul 13 19:22:07 2009 (4A5BC19F)
fffff880`00ec2000 fffff880`00ed1000 WDFLDR WDFLDR.SYS Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`02d46000 fffff880`02d4f000 wfplwf wfplwf.sys Mon Jul 13 20:09:26 2009 (4A5BCCB6)
fffff960`000e0000 fffff960`003f0000 win32k win32k.sys Tue Oct 19 23:08:46 2010 (4CBE5D3E)
fffff880`00f28000 fffff880`00f31000 WMILIB WMILIB.SYS Mon Jul 13 19:19:51 2009 (4A5BC117)
fffff880`01975000 fffff880`01996000 WudfPf WudfPf.sys Mon Jul 13 20:05:37 2009 (4A5BCBD1)
Unloaded modules:
fffff880`01975000 fffff880`01983000 crashdmp.sys
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 0000E000
fffff880`01983000 fffff880`0198f000 dump_ataport
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 0000C000
fffff880`0198f000 fffff880`01998000 dump_atapi.s
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 00009000
fffff880`01998000 fffff880`019ab000 dump_dumpfve
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 000130001. Here are the screenshots
2. I uninstalled SpeedFan
3. I uninstalled the CatalystControlCenter and ran the driver sweeper, but 10.9 doesn't work for me. As a result I installed the newest driver. I hope, I have nothing done wrong
2. I uninstalled SpeedFan
3. I uninstalled the CatalystControlCenter and ran the driver sweeper, but 10.9 doesn't work for me. As a result I installed the newest driver. I hope, I have nothing done wrong
Attachments
- Joined
- Sep 22, 2010
- Messages
- 613
- Reaction score
- 102
The RAM sticks are from the same pair and they are set right.
Catalyst 10.12 Preview is a notorious bsod maker:
http://forums.amd.com/game/messageview.cfm?catid=279&threadid=143930
Catalyst 10.12 Preview is a notorious bsod maker:
http://forums.amd.com/game/messageview.cfm?catid=279&threadid=143930
- Joined
- Sep 22, 2010
- Messages
- 613
- Reaction score
- 102
Replace Catalyst 10.12 with 11.1 WHQL,
http://www.guru3d.com/category/driversweeper/
Crash Dumps:
Drivers:
http://www.guru3d.com/category/driversweeper/
Crash Dumps:
Code:
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\a\Minidump\D M P\DMP\020411-19390-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7600 MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7600.16617.amd64fre.win7_gdr.100618-1621
Machine Name:
Kernel base = 0xfffff800`03053000 PsLoadedModuleList = 0xfffff800`03290e50
Debug session time: Fri Feb 4 12:47:13.620 2011 (UTC - 5:00)
System Uptime: 0 days 0:00:33.555
Loading Kernel Symbols
...............................................................
................................................................
...
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {0, 2, 0, fffff800030e32b3}
Probably caused by : ntkrnlmp.exe ( nt!KiPageFault+260 )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000000000, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff800030e32b3, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800032fb0e0
0000000000000000
CURRENT_IRQL: 2
FAULTING_IP:
nt!IopCompleteRequest+ae3
fffff800`030e32b3 488b09 mov rcx,qword ptr [rcx]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: nvvsvc.exe
IRP_ADDRESS: ffffffffffffff89
TRAP_FRAME: fffff880037b5150 -- (.trap 0xfffff880037b5150)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff880037b53e8 rbx=0000000000000000 rcx=0000000000000000
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff800030e32b3 rsp=fffff880037b52e0 rbp=fffff880037b5430
r8=fffffa8005938230 r9=fffff880037b53e0 r10=0000000000000002
r11=fffffa8005c28e00 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz ac po cy
nt!IopCompleteRequest+0xae3:
fffff800`030e32b3 488b09 mov rcx,qword ptr [rcx] ds:00000000`00000000=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff800030c2ca9 to fffff800030c3740
STACK_TEXT:
fffff880`037b5008 fffff800`030c2ca9 : 00000000`0000000a 00000000`00000000 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffff880`037b5010 fffff800`030c1920 : fffffa80`0554a420 fffffa80`0526d6f0 fffffa80`058e4010 fffff880`012b4ea4 : nt!KiBugCheckDispatch+0x69
fffff880`037b5150 fffff800`030e32b3 : 00000000`00000000 fffffa80`036346a8 fffffa80`053bdf68 00000000`00000000 : nt!KiPageFault+0x260
fffff880`037b52e0 fffff800`030a00c7 : 00000000`00000001 fffffa80`053bdfb0 fffffa80`03634600 fffff880`00000000 : nt!IopCompleteRequest+0xae3
fffff880`037b53b0 fffff800`030a0487 : fffffa80`05b32b30 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDeliverApc+0x1d7
fffff880`037b5430 fffff800`033a946a : 00000000`00000000 fffff800`00401802 00000000`00000000 fffffa80`05b27000 : nt!KiApcInterrupt+0xd7
fffff880`037b55c0 fffff800`0331eda3 : fffffa80`052b9070 fffffa80`05b27000 fffff8a0`00002000 fffff880`037b5758 : nt!ObpQueryNameString+0x56
fffff880`037b56c0 fffff800`0338043e : fffffa80`05b32b30 00000000`00000000 fffffa80`054ee060 00000000`00000001 : nt! ?? ::NNGAKEGL::`string'+0x210a4
fffff880`037b5860 fffff800`033a8cd4 : 000007ff`fffda000 fffff880`037b5be0 00000000`00000000 fffffa80`057ea090 : nt!PspExitProcess+0x4e
fffff880`037b58c0 fffff800`03381635 : 00000000`00000000 fffff800`033c2101 000007ff`fffda000 00000000`00000000 : nt!PspExitThread+0x834
fffff880`037b5980 fffff800`030a01db : fffffa80`0590b001 fffffa80`059ecb10 00000000`00000000 00000000`00000000 : nt!PsExitSpecialApc+0x1d
fffff880`037b59b0 fffff800`030a0620 : 00000000`001e11e0 fffff880`037b5a30 fffff800`0338174c 00000000`00000001 : nt!KiDeliverApc+0x2eb
fffff880`037b5a30 fffff800`030c2a37 : 00000000`0000044f 00000000`0108eb70 00000000`00000000 0000007f`ffffffff : nt!KiInitiateUserApc+0x70
fffff880`037b5b70 00000000`7709008a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9c
00000000`0108f508 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7709008a
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!KiPageFault+260
fffff800`030c1920 440f20c0 mov rax,cr8
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: nt!KiPageFault+260
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 4c1c44a9
FAILURE_BUCKET_ID: X64_0xA_nt!KiPageFault+260
BUCKET_ID: X64_0xA_nt!KiPageFault+260
Followup: MachineOwner
---------Drivers:
Code:
start end module name
fffff880`00f79000 fffff880`00fd0000 ACPI ACPI.sys Mon Jul 13 19:19:34 2009 (4A5BC106)
fffff880`02cfc000 fffff880`02d86000 afd afd.sys Mon Jul 13 19:21:40 2009 (4A5BC184)
fffff880`03bc8000 fffff880`03bde000 AgileVpn AgileVpn.sys Mon Jul 13 20:10:24 2009 (4A5BCCF0)
fffff880`00df0000 fffff880`00dfb000 amdxata amdxata.sys Tue May 19 13:56:59 2009 (4A12F2EB)
fffff880`051e8000 fffff880`051f0000 ASACPI ASACPI.sys Wed Jul 15 23:31:29 2009 (4A5E9F11)
fffff880`02dfa000 fffff880`02e00000 AsIO AsIO.sys Mon Aug 03 03:03:16 2009 (4A768BB4)
fffff880`02cf6000 fffff880`02cfc000 AsUpIO AsUpIO.sys Sun Jul 05 22:21:38 2009 (4A515FB2)
fffff880`00dbd000 fffff880`00dc6000 atapi atapi.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`00dc6000 fffff880`00df0000 ataport ataport.SYS Mon Jul 13 19:19:52 2009 (4A5BC118)
fffff880`03d81000 fffff880`03da1000 AtihdW76 AtihdW76.sys Wed Nov 17 07:02:04 2010 (4CE3C43C)
fffff880`0483e000 fffff880`0504f000 atikmdag atikmdag.sys Thu Nov 25 21:46:44 2010 (4CEF1F94)
fffff880`03ac0000 fffff880`03b0c000 atikmpag atikmpag.sys Thu Nov 25 21:16:47 2010 (4CEF188F)
fffff880`01880000 fffff880`01887000 Beep Beep.SYS Mon Jul 13 20:00:13 2009 (4A5BCA8D)
fffff880`0104a000 fffff880`0105b000 blbdrive blbdrive.sys Mon Jul 13 19:35:59 2009 (4A5BC4DF)
fffff960`00690000 fffff960`006b7000 cdd cdd.dll Tue Nov 02 00:59:22 2010 (4CCF9AAA)
fffff880`0181c000 fffff880`01846000 cdrom cdrom.sys Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`00ce3000 fffff880`00da3000 CI CI.dll Mon Jul 13 21:32:13 2009 (4A5BE01D)
fffff880`019af000 fffff880`019df000 CLASSPNP CLASSPNP.SYS Mon Jul 13 19:19:58 2009 (4A5BC11E)
fffff880`00c85000 fffff880`00ce3000 CLFS CLFS.SYS Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`01148000 fffff880`011bb000 cng cng.sys Mon Jul 13 19:49:40 2009 (4A5BC814)
fffff880`0482d000 fffff880`0483d000 CompositeBus CompositeBus.sys Mon Jul 13 20:00:33 2009 (4A5BCAA1)
fffff880`05fe0000 fffff880`05fee000 crashdmp crashdmp.sys Mon Jul 13 20:01:01 2009 (4A5BCABD)
fffff880`02cd8000 fffff880`02cf6000 dfsc dfsc.sys Mon Jul 13 19:23:44 2009 (4A5BC200)
fffff880`02cc9000 fffff880`02cd8000 discache discache.sys Mon Jul 13 19:37:18 2009 (4A5BC52E)
fffff880`01999000 fffff880`019af000 disk disk.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`03dde000 fffff880`03e00000 drmk drmk.sys Mon Jul 13 21:01:25 2009 (4A5BD8E5)
fffff880`05e00000 fffff880`05e09000 dump_atapi dump_atapi.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`05fee000 fffff880`05ffa000 dump_dumpata dump_dumpata.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`05e09000 fffff880`05e1c000 dump_dumpfve dump_dumpfve.sys Mon Jul 13 19:21:51 2009 (4A5BC18F)
fffff880`02cc3000 fffff880`02cc9000 dvdfabio dvdfabio.sys Tue Dec 07 00:19:28 2010 (4CFDC3E0)
fffff880`03c06000 fffff880`03c12000 Dxapi Dxapi.sys Mon Jul 13 19:38:28 2009 (4A5BC574)
fffff880`0504f000 fffff880`05143000 dxgkrnl dxgkrnl.sys Mon Nov 01 22:51:31 2010 (4CCF7CB3)
fffff880`05143000 fffff880`05189000 dxgmms1 dxgmms1.sys Mon Nov 01 22:50:56 2010 (4CCF7C90)
fffff880`010d6000 fffff880`010ea000 fileinfo fileinfo.sys Mon Jul 13 19:34:25 2009 (4A5BC481)
fffff880`0108a000 fffff880`010d6000 fltmgr fltmgr.sys Mon Jul 13 19:19:59 2009 (4A5BC11F)
fffff880`013ee000 fffff880`013f8000 Fs_Rec Fs_Rec.sys Mon Jul 13 19:19:45 2009 (4A5BC111)
fffff880`0195f000 fffff880`01999000 fvevol fvevol.sys Fri Sep 25 22:34:26 2009 (4ABD7DB2)
fffff880`01000000 fffff880`0104a000 fwpkclnt fwpkclnt.sys Mon Jul 13 19:21:08 2009 (4A5BC164)
fffff880`0194b000 fffff880`0195f000 gagp30kx gagp30kx.sys Mon Jul 13 19:38:43 2009 (4A5BC583)
fffff800`0300a000 fffff800`03053000 hal hal.dll Mon Jul 13 21:27:36 2009 (4A5BDF08)
fffff880`05189000 fffff880`051ad000 HDAudBus HDAudBus.sys Mon Jul 13 20:06:13 2009 (4A5BCBF5)
fffff880`03c20000 fffff880`03c39000 HIDCLASS HIDCLASS.SYS Mon Jul 13 20:06:21 2009 (4A5BCBFD)
fffff880`03c39000 fffff880`03c41080 HIDPARSE HIDPARSE.SYS Mon Jul 13 20:06:17 2009 (4A5BCBF9)
fffff880`03c12000 fffff880`03c20000 hidusb hidusb.sys Mon Jul 13 20:06:22 2009 (4A5BCBFE)
fffff880`01942000 fffff880`0194b000 hwpolicy hwpolicy.sys Mon Jul 13 19:19:22 2009 (4A5BC0FA)
fffff880`04800000 fffff880`0481e000 i8042prt i8042prt.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`00eb9000 fffff880`00ec1000 intelide intelide.sys Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`011bb000 fffff880`011d1000 intelppm intelppm.sys Mon Jul 13 19:19:25 2009 (4A5BC0FD)
fffff880`0481e000 fffff880`0482d000 kbdclass kbdclass.sys Mon Jul 13 19:19:50 2009 (4A5BC116)
fffff800`00bc6000 fffff800`00bc9000 kdcom kdcom.dll Tue Nov 30 09:40:39 2010 (4CF50CE7)
fffff880`03cbd000 fffff880`03d00000 ks ks.sys Wed Mar 03 23:32:25 2010 (4B8F37D9)
fffff880`013c3000 fffff880`013dd000 ksecdd ksecdd.sys Mon Jul 13 19:20:54 2009 (4A5BC156)
fffff880`0159a000 fffff880`015c5000 ksecpkg ksecpkg.sys Fri Dec 11 01:03:32 2009 (4B21E0B4)
fffff880`03c00000 fffff880`03c05200 ksthunk ksthunk.sys Mon Jul 13 20:00:19 2009 (4A5BCA93)
fffff880`03ca1000 fffff880`03cb6000 lltdio lltdio.sys Mon Jul 13 20:08:50 2009 (4A5BCC92)
fffff880`03c5d000 fffff880`03c80000 luafv luafv.sys Mon Jul 13 19:26:13 2009 (4A5BC295)
fffff880`00c2d000 fffff880`00c71000 mcupdate_GenuineIntel mcupdate_GenuineIntel.dll Mon Jul 13 21:29:10 2009 (4A5BDF66)
fffff880`03c4f000 fffff880`03c5d000 monitor monitor.sys Mon Jul 13 19:38:52 2009 (4A5BC58C)
fffff880`03bde000 fffff880`03bed000 mouclass mouclass.sys Mon Jul 13 19:19:50 2009 (4A5BC116)
fffff880`03c42000 fffff880`03c4f000 mouhid mouhid.sys Mon Jul 13 20:00:20 2009 (4A5BCA94)
fffff880`00da3000 fffff880`00dbd000 mountmgr mountmgr.sys Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`01846000 fffff880`01877000 MpFilter MpFilter.sys Tue Sep 14 20:19:28 2010 (4C901110)
fffff880`01412000 fffff880`0141d000 Msfs Msfs.SYS Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`00fd9000 fffff880`00fe3000 msisadrv msisadrv.sys Mon Jul 13 19:19:26 2009 (4A5BC0FE)
fffff880`010ea000 fffff880`01148000 msrpc msrpc.sys Mon Jul 13 19:21:32 2009 (4A5BC17C)
fffff880`02cb8000 fffff880`02cc3000 mssmbios mssmbios.sys Mon Jul 13 19:31:10 2009 (4A5BC3BE)
fffff880`01930000 fffff880`01942000 mup mup.sys Mon Jul 13 19:23:45 2009 (4A5BC201)
fffff880`01448000 fffff880`0153a000 ndis ndis.sys Mon Jul 13 19:21:40 2009 (4A5BC184)
fffff880`03a24000 fffff880`03a30000 ndistapi ndistapi.sys Mon Jul 13 20:10:00 2009 (4A5BCCD8)
fffff880`03a30000 fffff880`03a5f000 ndiswan ndiswan.sys Mon Jul 13 20:10:11 2009 (4A5BCCE3)
fffff880`03d6c000 fffff880`03d81000 NDProxy NDProxy.SYS Mon Jul 13 20:10:05 2009 (4A5BCCDD)
fffff880`02c00000 fffff880`02c0f000 netbios netbios.sys Mon Jul 13 20:09:26 2009 (4A5BCCB6)
fffff880`02d86000 fffff880`02dcb000 netbt netbt.sys Mon Jul 13 19:21:28 2009 (4A5BC178)
fffff880`0153a000 fffff880`0159a000 NETIO NETIO.SYS Thu Apr 08 22:43:59 2010 (4BBE946F)
fffff880`0141d000 fffff880`0142e000 Npfs Npfs.SYS Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`02cac000 fffff880`02cb8000 nsiproxy nsiproxy.sys Mon Jul 13 19:21:02 2009 (4A5BC15E)
fffff800`03053000 fffff800`0362f000 nt ntkrnlmp.exe Sat Jun 19 00:16:41 2010 (4C1C44A9)
fffff880`01220000 fffff880`013c3000 Ntfs Ntfs.sys Mon Jul 13 19:20:47 2009 (4A5BC14F)
fffff880`01877000 fffff880`01880000 Null Null.SYS Mon Jul 13 19:19:37 2009 (4A5BC109)
fffff880`02dd4000 fffff880`02dfa000 pacer pacer.sys Mon Jul 13 20:09:41 2009 (4A5BCCC5)
fffff880`051cb000 fffff880`051e8000 parport parport.sys Mon Jul 13 20:00:40 2009 (4A5BCAA8)
fffff880`00e33000 fffff880`00e48000 partmgr partmgr.sys Mon Jul 13 19:19:58 2009 (4A5BC11E)
fffff880`00e00000 fffff880`00e33000 pci pci.sys Mon Jul 13 19:19:51 2009 (4A5BC117)
fffff880`00ff0000 fffff880`01000000 PCIIDEX PCIIDEX.SYS Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`013dd000 fffff880`013ee000 pcw pcw.sys Mon Jul 13 19:19:27 2009 (4A5BC0FF)
fffff880`03da1000 fffff880`03dde000 portcls portcls.sys Mon Jul 13 20:06:27 2009 (4A5BCC03)
fffff880`00c71000 fffff880`00c85000 PSHED PSHED.dll Mon Jul 13 21:32:23 2009 (4A5BE027)
fffff880`03a00000 fffff880`03a24000 rasl2tp rasl2tp.sys Mon Jul 13 20:10:11 2009 (4A5BCCE3)
fffff880`03a5f000 fffff880`03a7a000 raspppoe raspppoe.sys Mon Jul 13 20:10:17 2009 (4A5BCCE9)
fffff880`03a7a000 fffff880`03a9b000 raspptp raspptp.sys Mon Jul 13 20:10:18 2009 (4A5BCCEA)
fffff880`03a9b000 fffff880`03ab5000 rassstp rassstp.sys Mon Jul 13 20:10:25 2009 (4A5BCCF1)
fffff880`02c5b000 fffff880`02cac000 rdbss rdbss.sys Mon Jul 13 19:24:09 2009 (4A5BC219)
fffff880`01895000 fffff880`0189e000 RDPCDD RDPCDD.sys Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`01400000 fffff880`01409000 rdpencdd rdpencdd.sys Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`01409000 fffff880`01412000 rdprefmp rdprefmp.sys Mon Jul 13 20:16:35 2009 (4A5BCE63)
fffff880`018f6000 fffff880`01930000 rdyboost rdyboost.sys Mon Jul 13 19:34:34 2009 (4A5BC48A)
fffff880`019df000 fffff880`019f7000 rspndr rspndr.sys Mon Jul 13 20:08:50 2009 (4A5BCC92)
fffff880`03b0c000 fffff880`03b72000 Rt64win7 Rt64win7.sys Tue Nov 30 01:01:28 2010 (4CF49338)
fffff880`011d1000 fffff880`01200000 SCSIPORT SCSIPORT.SYS Mon Jul 13 20:01:04 2009 (4A5BCAC0)
fffff880`051f0000 fffff880`051fc000 serenum serenum.sys Mon Jul 13 20:00:33 2009 (4A5BCAA1)
fffff880`02c0f000 fffff880`02c2c000 serial serial.sys Mon Jul 13 20:00:40 2009 (4A5BCAA8)
fffff880`018ee000 fffff880`018f6000 spldr spldr.sys Mon May 11 12:56:27 2009 (4A0858BB)
fffff880`051fc000 fffff880`051fd480 swenum swenum.sys Mon Jul 13 20:00:18 2009 (4A5BCA92)
fffff880`01601000 fffff880`017fe000 tcpip tcpip.sys Sun Jun 13 23:39:04 2010 (4C15A458)
fffff880`0142e000 fffff880`0143b000 TDI TDI.SYS Mon Jul 13 19:21:18 2009 (4A5BC16E)
fffff880`01200000 fffff880`0121e000 tdx tdx.sys Mon Jul 13 19:21:15 2009 (4A5BC16B)
fffff880`02c47000 fffff880`02c5b000 termdd termdd.sys Mon Jul 13 20:16:36 2009 (4A5BCE64)
fffff960`00530000 fffff960`0053a000 TSDDD TSDDD.dll unavailable (00000000)
fffff880`0105b000 fffff880`01081000 tunnel tunnel.sys Mon Jul 13 20:09:37 2009 (4A5BCCC1)
fffff880`03d00000 fffff880`03d12000 umbus umbus.sys Mon Jul 13 20:06:56 2009 (4A5BCC20)
fffff880`05e1c000 fffff880`05e1df00 USBD USBD.SYS Mon Jul 13 20:06:23 2009 (4A5BCBFF)
fffff880`051ba000 fffff880`051cb000 usbehci usbehci.sys Mon Jul 13 20:06:30 2009 (4A5BCC06)
fffff880`03d12000 fffff880`03d6c000 usbhub usbhub.sys Mon Jul 13 20:07:09 2009 (4A5BCC2D)
fffff880`03b72000 fffff880`03bc8000 USBPORT USBPORT.SYS Mon Jul 13 20:06:31 2009 (4A5BCC07)
fffff880`051ad000 fffff880`051ba000 usbuhci usbuhci.sys Mon Jul 13 20:06:27 2009 (4A5BCC03)
fffff880`03bed000 fffff880`03bfb000 vdrive vdrive.sys Tue Dec 07 00:19:28 2010 (4CFDC3E0)
fffff880`00fe3000 fffff880`00ff0000 vdrvroot vdrvroot.sys Mon Jul 13 20:01:31 2009 (4A5BCADB)
fffff880`01887000 fffff880`01895000 vga vga.sys Mon Jul 13 19:38:47 2009 (4A5BC587)
fffff880`05e1f000 fffff880`05fe0000 viahduaa viahduaa.sys Wed Aug 04 03:51:53 2010 (4C591C19)
fffff880`015c5000 fffff880`015ea000 VIDEOPRT VIDEOPRT.SYS Mon Jul 13 19:38:51 2009 (4A5BC58B)
fffff880`00e48000 fffff880`00e5d000 volmgr volmgr.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`00e5d000 fffff880`00eb9000 volmgrx volmgrx.sys Mon Jul 13 19:20:33 2009 (4A5BC141)
fffff880`018a2000 fffff880`018ee000 volsnap volsnap.sys Mon Jul 13 19:20:08 2009 (4A5BC128)
fffff880`02c2c000 fffff880`02c47000 wanarp wanarp.sys Mon Jul 13 20:10:21 2009 (4A5BCCED)
fffff880`015ea000 fffff880`015fa000 watchdog watchdog.sys Mon Jul 13 19:37:35 2009 (4A5BC53F)
fffff880`00ec6000 fffff880`00f6a000 Wdf01000 Wdf01000.sys Mon Jul 13 19:22:07 2009 (4A5BC19F)
fffff880`00f6a000 fffff880`00f79000 WDFLDR WDFLDR.SYS Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`02dcb000 fffff880`02dd4000 wfplwf wfplwf.sys Mon Jul 13 20:09:26 2009 (4A5BCCB6)
fffff960`00060000 fffff960`00370000 win32k win32k.sys Tue Oct 19 23:08:46 2010 (4CBE5D3E)
fffff880`00fd0000 fffff880`00fd9000 WMILIB WMILIB.SYS Mon Jul 13 19:19:51 2009 (4A5BC117)
fffff880`03c80000 fffff880`03ca1000 WudfPf WudfPf.sys Mon Jul 13 20:05:37 2009 (4A5BCBD1)
Unloaded modules:
fffff880`019df000 fffff880`019ed000 crashdmp.sys
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 0000E000
fffff880`019ed000 fffff880`019f9000 dump_ataport
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 0000C000
fffff880`01800000 fffff880`01809000 dump_atapi.s
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 00009000
fffff880`01809000 fffff880`0181c000 dump_dumpfve
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 00013000- Joined
- Sep 22, 2010
- Messages
- 613
- Reaction score
- 102
BUGCHECK_STR: 0xA
PROCESS_NAME: MpCmdRun.exe <--- Windows Defender
0xA_tcpip!CreateProcessNotifyRoutineEx
1. https://www.w7forums.com/memtest86-memory-testing-t9067.html
10 passes overnight
2. If no errors, then backup your data and reinstall the OS. It might be something with the configurations.
PROCESS_NAME: MpCmdRun.exe <--- Windows Defender
0xA_tcpip!CreateProcessNotifyRoutineEx
1. https://www.w7forums.com/memtest86-memory-testing-t9067.html
10 passes overnight
2. If no errors, then backup your data and reinstall the OS. It might be something with the configurations.
Code:
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\a\Minidump\D M P\DMP\020511-24928-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*[url]http://msdl.microsoft.com/download/symbols[/url]
Executable search path is:
Windows 7 Kernel Version 7600 MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7600.16617.amd64fre.win7_gdr.100618-1621
Machine Name:
Kernel base = 0xfffff800`03251000 PsLoadedModuleList = 0xfffff800`0348ee50
Debug session time: Sat Feb 5 14:53:28.298 2011 (UTC - 5:00)
System Uptime: 0 days 0:00:39.234
Loading Kernel Symbols
...............................................................
................................................................
...........
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {100000001, 2, 0, fffff800032e12b3}
Probably caused by : tcpip.sys ( tcpip!CreateProcessNotifyRoutineEx+66 )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000100000001, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff800032e12b3, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff800034f90e0
0000000100000001
CURRENT_IRQL: 2
FAULTING_IP:
nt!IopCompleteRequest+ae3
fffff800`032e12b3 488b09 mov rcx,qword ptr [rcx]
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: MpCmdRun.exe
IRP_ADDRESS: ffffffffffffff89
TRAP_FRAME: fffff880046db390 -- (.trap 0xfffff880046db390)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff880046db6e8 rbx=0000000000000000 rcx=0000000100000001
rdx=0000000100000001 rsi=0000000000000000 rdi=0000000000000000
rip=fffff800032e12b3 rsp=fffff880046db520 rbp=fffff880046db670
r8=fffffa80059a4740 r9=fffff880046db620 r10=0000000000000002
r11=fffffa8005d8bd30 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz ac pe cy
nt!IopCompleteRequest+0xae3:
fffff800`032e12b3 488b09 mov rcx,qword ptr [rcx] ds:5730:00000001`00000001=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff800032c0ca9 to fffff800032c1740
STACK_TEXT:
fffff880`046db248 fffff800`032c0ca9 : 00000000`0000000a 00000001`00000001 00000000`00000002 00000000`00000000 : nt!KeBugCheckEx
fffff880`046db250 fffff800`032bf920 : fffffa80`00000000 fffffa80`05e75590 fffffa80`045b9c20 00000000`00000200 : nt!KiBugCheckDispatch+0x69
fffff880`046db390 fffff800`032e12b3 : 00000000`00000000 00000000`00000000 00000000`0000000d fffff900`c0200138 : nt!KiPageFault+0x260
fffff880`046db520 fffff800`0329e0c7 : 00000000`00000001 00000000`00000000 00000000`00000000 fffffa80`00000000 : nt!IopCompleteRequest+0xae3
fffff880`046db5f0 fffff800`0329e487 : fffffa80`05e38190 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDeliverApc+0x1d7
fffff880`046db670 fffff800`032cec7a : fffff880`01788520 fffff8a0`00097110 fffffa80`05e76ad0 fffff880`046db870 : nt!KiApcInterrupt+0xd7
fffff880`046db800 fffff880`0164e086 : fffffa80`05e38190 fffffa80`05e55730 00000000`00000001 fffff8a0`0009ce60 : nt!KeReleaseSpinLock+0x2a
fffff880`046db830 fffff800`0357e58d : fffffa80`05e55730 00000000`00000001 fffffa80`050000ff fffffa80`05e38190 : tcpip!CreateProcessNotifyRoutineEx+0x66
fffff880`046db860 fffff800`035a6cd4 : 000007ff`fffda000 fffff880`046dbbe0 00000000`00000000 fffffa80`05524a60 : nt!PspExitProcess+0x19d
fffff880`046db8c0 fffff800`0357f635 : 00000000`00000000 fffffa80`05e76a01 000007ff`fffda000 00000000`00000000 : nt!PspExitThread+0x834
fffff880`046db980 fffff800`0329e1db : 00000000`00000000 00000000`00000000 fffffa80`055309e0 00000000`00000000 : nt!PsExitSpecialApc+0x1d
fffff880`046db9b0 fffff800`0329e620 : 00000000`002cb3c0 fffff880`046dba30 fffff800`0357f74c 00000000`00000001 : nt!KiDeliverApc+0x2eb
fffff880`046dba30 fffff800`032c0a37 : ffffffff`ffffffff 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiInitiateUserApc+0x70
fffff880`046dbb70 00000000`775bfdba : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9c
00000000`0110f088 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x775bfdba
STACK_COMMAND: kb
FOLLOWUP_IP:
tcpip!CreateProcessNotifyRoutineEx+66
fffff880`0164e086 488d4b30 lea rcx,[rbx+30h]
SYMBOL_STACK_INDEX: 7
SYMBOL_NAME: tcpip!CreateProcessNotifyRoutineEx+66
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: tcpip
IMAGE_NAME: tcpip.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4c15a458
FAILURE_BUCKET_ID: X64_0xA_tcpip!CreateProcessNotifyRoutineEx+66
BUCKET_ID: X64_0xA_tcpip!CreateProcessNotifyRoutineEx+66
fffff880`0609b000 fffff880`060f5000 acedrv11 acedrv11.sys Wed Feb 24 05:20:17 2010 (4B84FD61)
fffff880`00fa0000 fffff880`00ff7000 ACPI ACPI.sys Mon Jul 13 19:19:34 2009 (4A5BC106)
fffff880`02c00000 fffff880`02c8a000 afd afd.sys Mon Jul 13 19:21:40 2009 (4A5BC184)
fffff880`03fcb000 fffff880`03fe1000 AgileVpn AgileVpn.sys Mon Jul 13 20:10:24 2009 (4A5BCCF0)
fffff880`00dd7000 fffff880`00de2000 amdxata amdxata.sys Tue May 19 13:56:59 2009 (4A12F2EB)
fffff880`048a5000 fffff880`048ad000 ASACPI ASACPI.sys Wed Jul 15 23:31:29 2009 (4A5E9F11)
fffff880`02dfa000 fffff880`02e00000 AsIO AsIO.sys Mon Aug 03 03:03:16 2009 (4A768BB4)
fffff880`02df4000 fffff880`02dfa000 AsUpIO AsUpIO.sys Sun Jul 05 22:21:38 2009 (4A515FB2)
fffff880`00c8e000 fffff880`00c97000 atapi atapi.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`00dad000 fffff880`00dd7000 ataport ataport.SYS Mon Jul 13 19:19:52 2009 (4A5BC118)
fffff880`041cb000 fffff880`041eb000 AtihdW76 AtihdW76.sys Wed Nov 17 07:02:04 2010 (4CE3C43C)
fffff880`048b3000 fffff880`050ea000 atikmdag atikmdag.sys Tue Jan 04 21:48:52 2011 (4D23DC14)
fffff880`03e94000 fffff880`03ee1000 atikmpag atikmpag.sys Tue Jan 04 21:19:38 2011 (4D23D53A)
fffff880`0199d000 fffff880`019a4000 Beep Beep.SYS Mon Jul 13 20:00:13 2009 (4A5BCA8D)
fffff880`01850000 fffff880`01861000 blbdrive blbdrive.sys Mon Jul 13 19:35:59 2009 (4A5BC4DF)
fffff880`02b6d000 fffff880`02b8b000 bowser bowser.sys Mon Jul 13 19:23:50 2009 (4A5BC206)
fffff960`00630000 fffff960`00657000 cdd cdd.dll unavailable (00000000)
fffff880`01939000 fffff880`01963000 cdrom cdrom.sys Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`00e2d000 fffff880`00eed000 CI CI.dll Mon Jul 13 21:32:13 2009 (4A5BE01D)
fffff880`018d3000 fffff880`01903000 CLASSPNP CLASSPNP.SYS Mon Jul 13 19:19:58 2009 (4A5BC11E)
fffff880`00d07000 fffff880`00d65000 CLFS CLFS.SYS Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`010fa000 fffff880`0116d000 cng cng.sys Mon Jul 13 19:49:40 2009 (4A5BC814)
fffff880`03fbb000 fffff880`03fcb000 CompositeBus CompositeBus.sys Mon Jul 13 20:00:33 2009 (4A5BCAA1)
fffff880`05fcd000 fffff880`05fdb000 crashdmp crashdmp.sys Mon Jul 13 20:01:01 2009 (4A5BCABD)
fffff880`02dd6000 fffff880`02df4000 dfsc dfsc.sys Mon Jul 13 19:23:44 2009 (4A5BC200)
fffff880`02dc7000 fffff880`02dd6000 discache discache.sys Mon Jul 13 19:37:18 2009 (4A5BC52E)
fffff880`00de2000 fffff880`00df8000 disk disk.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`0403d000 fffff880`0405f000 drmk drmk.sys Mon Jul 13 21:01:25 2009 (4A5BD8E5)
fffff880`05fe7000 fffff880`05ff0000 dump_atapi dump_atapi.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`05fdb000 fffff880`05fe7000 dump_dumpata dump_dumpata.sys Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`04065000 fffff880`04078000 dump_dumpfve dump_dumpfve.sys Mon Jul 13 19:21:51 2009 (4A5BC18F)
fffff880`02dc1000 fffff880`02dc7000 dvdfabio dvdfabio.sys Tue Dec 07 00:19:28 2010 (4CFDC3E0)
fffff880`05ff0000 fffff880`05ffc000 Dxapi Dxapi.sys Mon Jul 13 19:38:28 2009 (4A5BC574)
fffff880`050ea000 fffff880`051de000 dxgkrnl dxgkrnl.sys Mon Nov 01 22:51:31 2010 (4CCF7CB3)
fffff880`04800000 fffff880`04846000 dxgmms1 dxgmms1.sys Mon Nov 01 22:50:56 2010 (4CCF7C90)
fffff880`01088000 fffff880`0109c000 fileinfo fileinfo.sys Mon Jul 13 19:34:25 2009 (4A5BC481)
fffff880`0103c000 fffff880`01088000 fltmgr fltmgr.sys Mon Jul 13 19:19:59 2009 (4A5BC11F)
fffff880`013d4000 fffff880`013de000 Fs_Rec Fs_Rec.sys Mon Jul 13 19:19:45 2009 (4A5BC111)
fffff880`01000000 fffff880`0103a000 fvevol fvevol.sys Fri Sep 25 22:34:26 2009 (4ABD7DB2)
fffff880`0148b000 fffff880`014d5000 fwpkclnt fwpkclnt.sys Mon Jul 13 19:21:08 2009 (4A5BC164)
fffff880`013de000 fffff880`013f2000 gagp30kx gagp30kx.sys Mon Jul 13 19:38:43 2009 (4A5BC583)
fffff800`03208000 fffff800`03251000 hal hal.dll Mon Jul 13 21:27:36 2009 (4A5BDF08)
fffff880`04846000 fffff880`0486a000 HDAudBus HDAudBus.sys Mon Jul 13 20:06:13 2009 (4A5BCBF5)
fffff880`04086000 fffff880`0409f000 HIDCLASS HIDCLASS.SYS Mon Jul 13 20:06:21 2009 (4A5BCBFD)
fffff880`05e00000 fffff880`05e08080 HIDPARSE HIDPARSE.SYS Mon Jul 13 20:06:17 2009 (4A5BCBF9)
fffff880`04078000 fffff880`04086000 hidusb hidusb.sys Mon Jul 13 20:06:22 2009 (4A5BCBFE)
fffff880`02aa5000 fffff880`02b6d000 HTTP HTTP.sys Mon Jul 13 19:22:16 2009 (4A5BC1A8)
fffff880`015f0000 fffff880`015f9000 hwpolicy hwpolicy.sys Mon Jul 13 19:19:22 2009 (4A5BC0FA)
fffff880`03f9d000 fffff880`03fbb000 i8042prt i8042prt.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`00c5c000 fffff880`00c64000 intelide intelide.sys Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`01887000 fffff880`0189d000 intelppm intelppm.sys Mon Jul 13 19:19:25 2009 (4A5BC0FD)
fffff880`051ea000 fffff880`051f9000 kbdclass kbdclass.sys Mon Jul 13 19:19:50 2009 (4A5BC116)
fffff800`00bc5000 fffff800`00bc8000 kdcom kdcom.dll Tue Nov 30 09:40:39 2010 (4CF50CE7)
fffff880`04107000 fffff880`0414a000 ks ks.sys Wed Mar 03 23:32:25 2010 (4B8F37D9)
fffff880`013a9000 fffff880`013c3000 ksecdd ksecdd.sys Mon Jul 13 19:20:54 2009 (4A5BC156)
fffff880`01460000 fffff880`0148b000 ksecpkg ksecpkg.sys Fri Dec 11 01:03:32 2009 (4B21E0B4)
fffff880`0405f000 fffff880`04064200 ksthunk ksthunk.sys Mon Jul 13 20:00:19 2009 (4A5BCA93)
fffff880`02a78000 fffff880`02a8d000 lltdio lltdio.sys Mon Jul 13 20:08:50 2009 (4A5BCC92)
fffff880`01903000 fffff880`01926000 luafv luafv.sys Mon Jul 13 19:26:13 2009 (4A5BC295)
fffff880`00caf000 fffff880`00cf3000 mcupdate_GenuineIntel mcupdate_GenuineIntel.dll Mon Jul 13 21:29:10 2009 (4A5BDF66)
fffff880`040ac000 fffff880`040ba000 monitor monitor.sys Mon Jul 13 19:38:52 2009 (4A5BC58C)
fffff880`03fe1000 fffff880`03ff0000 mouclass mouclass.sys Mon Jul 13 19:19:50 2009 (4A5BC116)
fffff880`0409f000 fffff880`040ac000 mouhid mouhid.sys Mon Jul 13 20:00:20 2009 (4A5BCA94)
fffff880`00c74000 fffff880`00c8e000 mountmgr mountmgr.sys Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`01963000 fffff880`01994000 MpFilter MpFilter.sys Tue Sep 14 20:19:28 2010 (4C901110)
fffff880`060f5000 fffff880`06105000 MpNWMon MpNWMon.sys Tue Sep 14 20:19:30 2010 (4C901112)
fffff880`02b8b000 fffff880`02ba3000 mpsdrv mpsdrv.sys Mon Jul 13 20:08:25 2009 (4A5BCC79)
fffff880`02ba3000 fffff880`02bd0000 mrxsmb mrxsmb.sys Sat Feb 27 02:52:19 2010 (4B88CF33)
fffff880`02a00000 fffff880`02a4e000 mrxsmb10 mrxsmb10.sys Sat Feb 27 02:52:28 2010 (4B88CF3C)
fffff880`02bd0000 fffff880`02bf3000 mrxsmb20 mrxsmb20.sys Sat Feb 27 02:52:26 2010 (4B88CF3A)
fffff880`01809000 fffff880`01814000 Msfs Msfs.SYS Mon Jul 13 19:19:47 2009 (4A5BC113)
fffff880`00e00000 fffff880`00e0a000 msisadrv msisadrv.sys Mon Jul 13 19:19:26 2009 (4A5BC0FE)
fffff880`0109c000 fffff880`010fa000 msrpc msrpc.sys Mon Jul 13 19:21:32 2009 (4A5BC17C)
fffff880`02db6000 fffff880`02dc1000 mssmbios mssmbios.sys Mon Jul 13 19:31:10 2009 (4A5BC3BE)
fffff880`015de000 fffff880`015f0000 mup mup.sys Mon Jul 13 19:23:45 2009 (4A5BC201)
fffff880`014ec000 fffff880`015de000 ndis ndis.sys Mon Jul 13 19:21:40 2009 (4A5BC184)
fffff880`03e24000 fffff880`03e30000 ndistapi ndistapi.sys Mon Jul 13 20:10:00 2009 (4A5BCCD8)
fffff880`03e30000 fffff880`03e5f000 ndiswan ndiswan.sys Mon Jul 13 20:10:11 2009 (4A5BCCE3)
fffff880`041b6000 fffff880`041cb000 NDProxy NDProxy.SYS Mon Jul 13 20:10:05 2009 (4A5BCCDD)
fffff880`02cfe000 fffff880`02d0d000 netbios netbios.sys Mon Jul 13 20:09:26 2009 (4A5BCCB6)
fffff880`02c8a000 fffff880`02ccf000 netbt netbt.sys Mon Jul 13 19:21:28 2009 (4A5BC178)
fffff880`01400000 fffff880`01460000 NETIO NETIO.SYS Thu Apr 08 22:43:59 2010 (4BBE946F)
fffff880`01814000 fffff880`01825000 Npfs Npfs.SYS Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`02daa000 fffff880`02db6000 nsiproxy nsiproxy.sys Mon Jul 13 19:21:02 2009 (4A5BC15E)
fffff800`03251000 fffff800`0382d000 nt ntkrnlmp.exe Sat Jun 19 00:16:41 2010 (4C1C44A9)
fffff880`01206000 fffff880`013a9000 Ntfs Ntfs.sys Mon Jul 13 19:20:47 2009 (4A5BC14F)
fffff880`01994000 fffff880`0199d000 Null Null.SYS Mon Jul 13 19:19:37 2009 (4A5BC109)
fffff880`02cd8000 fffff880`02cfe000 pacer pacer.sys Mon Jul 13 20:09:41 2009 (4A5BCCC5)
fffff880`04888000 fffff880`048a5000 parport parport.sys Mon Jul 13 20:00:40 2009 (4A5BCAA8)
fffff880`00e17000 fffff880`00e2c000 partmgr partmgr.sys Mon Jul 13 19:19:58 2009 (4A5BC11E)
fffff880`00d65000 fffff880`00d98000 pci pci.sys Mon Jul 13 19:19:51 2009 (4A5BC117)
fffff880`00c64000 fffff880`00c74000 PCIIDEX PCIIDEX.SYS Mon Jul 13 19:19:48 2009 (4A5BC114)
fffff880`013c3000 fffff880`013d4000 pcw pcw.sys Mon Jul 13 19:19:27 2009 (4A5BC0FF)
fffff880`04000000 fffff880`0403d000 portcls portcls.sys Mon Jul 13 20:06:27 2009 (4A5BCC03)
fffff880`00cf3000 fffff880`00d07000 PSHED PSHED.dll Mon Jul 13 21:32:23 2009 (4A5BE027)
fffff880`03e00000 fffff880`03e24000 rasl2tp rasl2tp.sys Mon Jul 13 20:10:11 2009 (4A5BCCE3)
fffff880`03e5f000 fffff880`03e7a000 raspppoe raspppoe.sys Mon Jul 13 20:10:17 2009 (4A5BCCE9)
fffff880`0189d000 fffff880`018be000 raspptp raspptp.sys Mon Jul 13 20:10:18 2009 (4A5BCCEA)
fffff880`03e7a000 fffff880`03e94000 rassstp rassstp.sys Mon Jul 13 20:10:25 2009 (4A5BCCF1)
fffff880`02d59000 fffff880`02daa000 rdbss rdbss.sys Mon Jul 13 19:24:09 2009 (4A5BC219)
fffff880`019e7000 fffff880`019f0000 RDPCDD RDPCDD.sys Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`019f0000 fffff880`019f9000 rdpencdd rdpencdd.sys Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`01800000 fffff880`01809000 rdprefmp rdprefmp.sys Mon Jul 13 20:16:35 2009 (4A5BCE63)
fffff880`011b9000 fffff880`011f3000 rdyboost rdyboost.sys Mon Jul 13 19:34:34 2009 (4A5BC48A)
fffff880`02a8d000 fffff880`02aa5000 rspndr rspndr.sys Mon Jul 13 20:08:50 2009 (4A5BCC92)
fffff880`03ee1000 fffff880`03f47000 Rt64win7 Rt64win7.sys Tue Nov 30 01:01:28 2010 (4CF49338)
fffff880`040d6000 fffff880`04105000 SCSIPORT SCSIPORT.SYS Mon Jul 13 20:01:04 2009 (4A5BCAC0)
fffff880`051de000 fffff880`051ea000 serenum serenum.sys Mon Jul 13 20:00:33 2009 (4A5BCAA1)
fffff880`02d0d000 fffff880`02d2a000 serial serial.sys Mon Jul 13 20:00:40 2009 (4A5BCAA8)
fffff880`014d5000 fffff880`014dd000 spldr spldr.sys Mon May 11 12:56:27 2009 (4A0858BB)
fffff880`04105000 fffff880`04106480 swenum swenum.sys Mon Jul 13 20:00:18 2009 (4A5BCA92)
fffff880`01600000 fffff880`017fd000 tcpip tcpip.sys Sun Jun 13 23:39:04 2010 (4C15A458)
fffff880`01843000 fffff880`01850000 TDI TDI.SYS Mon Jul 13 19:21:18 2009 (4A5BC16E)
fffff880`01825000 fffff880`01843000 tdx tdx.sys Mon Jul 13 19:21:15 2009 (4A5BC16B)
fffff880`02d45000 fffff880`02d59000 termdd termdd.sys Mon Jul 13 20:16:36 2009 (4A5BCE64)
fffff960`00570000 fffff960`0057a000 TSDDD TSDDD.dll Mon Jul 13 20:16:34 2009 (4A5BCE62)
fffff880`01861000 fffff880`01887000 tunnel tunnel.sys Mon Jul 13 20:09:37 2009 (4A5BCCC1)
fffff880`0414a000 fffff880`0415c000 umbus umbus.sys Mon Jul 13 20:06:56 2009 (4A5BCC20)
fffff880`05e09000 fffff880`05e0af00 USBD USBD.SYS Mon Jul 13 20:06:23 2009 (4A5BCBFF)
fffff880`04877000 fffff880`04888000 usbehci usbehci.sys Mon Jul 13 20:06:30 2009 (4A5BCC06)
fffff880`0415c000 fffff880`041b6000 usbhub usbhub.sys Mon Jul 13 20:07:09 2009 (4A5BCC2D)
fffff880`03f47000 fffff880`03f9d000 USBPORT USBPORT.SYS Mon Jul 13 20:06:31 2009 (4A5BCC07)
fffff880`0486a000 fffff880`04877000 usbuhci usbuhci.sys Mon Jul 13 20:06:27 2009 (4A5BCC03)
fffff880`03ff0000 fffff880`03ffe000 vdrive vdrive.sys Tue Dec 07 00:19:28 2010 (4CFDC3E0)
fffff880`00e0a000 fffff880`00e17000 vdrvroot vdrvroot.sys Mon Jul 13 20:01:31 2009 (4A5BCADB)
fffff880`019a4000 fffff880`019b2000 vga vga.sys Mon Jul 13 19:38:47 2009 (4A5BC587)
fffff880`05e0c000 fffff880`05fcd000 viahduaa viahduaa.sys Wed Aug 04 03:51:53 2010 (4C591C19)
fffff880`019b2000 fffff880`019d7000 VIDEOPRT VIDEOPRT.SYS Mon Jul 13 19:38:51 2009 (4A5BC58B)
fffff880`00d98000 fffff880`00dad000 volmgr volmgr.sys Mon Jul 13 19:19:57 2009 (4A5BC11D)
fffff880`00c00000 fffff880`00c5c000 volmgrx volmgrx.sys Mon Jul 13 19:20:33 2009 (4A5BC141)
fffff880`0116d000 fffff880`011b9000 volsnap volsnap.sys Mon Jul 13 19:20:08 2009 (4A5BC128)
fffff880`02d2a000 fffff880`02d45000 wanarp wanarp.sys Mon Jul 13 20:10:21 2009 (4A5BCCED)
fffff880`019d7000 fffff880`019e7000 watchdog watchdog.sys Mon Jul 13 19:37:35 2009 (4A5BC53F)
fffff880`00eed000 fffff880`00f91000 Wdf01000 Wdf01000.sys Mon Jul 13 19:22:07 2009 (4A5BC19F)
fffff880`00f91000 fffff880`00fa0000 WDFLDR WDFLDR.SYS Mon Jul 13 19:19:54 2009 (4A5BC11A)
fffff880`02ccf000 fffff880`02cd8000 wfplwf wfplwf.sys Mon Jul 13 20:09:26 2009 (4A5BCCB6)
fffff960`000b0000 fffff960`003c0000 win32k win32k.sys Tue Oct 19 23:08:46 2010 (4CBE5D3E)
fffff880`00ff7000 fffff880`01000000 WMILIB WMILIB.SYS Mon Jul 13 19:19:51 2009 (4A5BC117)
fffff880`02a57000 fffff880`02a78000 WudfPf WudfPf.sys Mon Jul 13 20:05:37 2009 (4A5BCBD1)
Unloaded modules:
fffff880`01903000 fffff880`01911000 crashdmp.sys
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 0000E000
fffff880`01911000 fffff880`0191d000 dump_ataport
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 0000C000
fffff880`0191d000 fffff880`01926000 dump_atapi.s
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 00009000
fffff880`01926000 fffff880`01939000 dump_dumpfve
Timestamp: unavailable (00000000)
Checksum: 00000000
ImageSize: 00013000