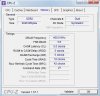
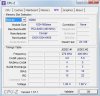
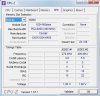
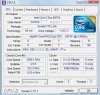
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\DMP\Mini042511-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6002 (Service Pack 2) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 6002.18160.amd64fre.vistasp2_gdr.091208-0542
Machine Name:
Kernel base = 0xfffff800`02406000 PsLoadedModuleList = 0xfffff800`025cadd0
Debug session time: Mon Apr 25 01:25:18.944 2011 (UTC - 4:00)
System Uptime: 0 days 5:30:42.964
Loading Kernel Symbols
...............................................................
................................................................
.......
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 19, {20, fffffa8005a3ba20, fffffa8005a3bf90, 457e4a0}
Unable to load image \SystemRoot\System32\drivers\tcpip.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for tcpip.sys
*** ERROR: Module load completed but symbols could not be loaded for tcpip.sys
Probably caused by : NETIO.SYS ( NETIO!NetioDereferenceNetBufferListChain+137 )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 0000000000000020, a pool block header size is corrupt.
Arg2: fffffa8005a3ba20, The pool entry we were looking for within the page.
Arg3: fffffa8005a3bf90, The next pool entry.
Arg4: 000000000457e4a0, (reserved)
Debugging Details:
------------------
BUGCHECK_STR: 0x19_20
POOL_ADDRESS: GetPointerFromAddress: unable to read from fffff8000262d080
fffffa8005a3ba20
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
PROCESS_NAME: System
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff8000253946a to fffff80002460450
STACK_TEXT:
fffff800`03699c88 fffff800`0253946a : 00000000`00000019 00000000`00000020 fffffa80`05a3ba20 fffffa80`05a3bf90 : nt!KeBugCheckEx
fffff800`03699c90 fffffa60`00e8390f : 00000000`ffffff6a 00000001`00000024 00000000`00000074 fffffa60`7ffffa80 : nt!ExDeferredFreePool+0x9e3
fffff800`03699d40 00000000`ffffff6a : 00000001`00000024 00000000`00000074 fffffa60`7ffffa80 00000000`00000001 : tcpip+0x7990f
fffff800`03699d48 00000001`00000024 : 00000000`00000074 fffffa60`7ffffa80 00000000`00000001 fffffa80`05a3b860 : 0xffffff6a
fffff800`03699d50 00000000`00000074 : fffffa60`7ffffa80 00000000`00000001 fffffa80`05a3b860 fffffa80`045e01a0 : 0x1`00000024
fffff800`03699d58 fffffa60`7ffffa80 : 00000000`00000001 fffffa80`05a3b860 fffffa80`045e01a0 fffffa60`00b438e7 : 0x74
fffff800`03699d60 00000000`00000001 : fffffa80`05a3b860 fffffa80`045e01a0 fffffa60`00b438e7 fffffa80`04b74760 : 0xfffffa60`7ffffa80
fffff800`03699d68 fffffa80`05a3b860 : fffffa80`045e01a0 fffffa60`00b438e7 fffffa80`04b74760 00000000`00000001 : 0x1
fffff800`03699d70 fffffa80`045e01a0 : fffffa60`00b438e7 fffffa80`04b74760 00000000`00000001 00000000`00000001 : 0xfffffa80`05a3b860
fffff800`03699d78 fffffa60`00b438e7 : fffffa80`04b74760 00000000`00000001 00000000`00000001 fffffa80`045e0050 : 0xfffffa80`045e01a0
fffff800`03699d80 fffffa60`00e716dc : fffff800`03699eb0 fffffa80`045e0001 00000000`00000000 00000000`00000000 : NETIO!NetioDereferenceNetBufferListChain+0x137
fffff800`03699e40 fffff800`03699eb0 : fffffa80`045e0001 00000000`00000000 00000000`00000000 fffffa80`04b741f0 : tcpip+0x676dc
fffff800`03699e48 fffffa80`045e0001 : 00000000`00000000 00000000`00000000 fffffa80`04b741f0 fffffa60`00c0b299 : 0xfffff800`03699eb0
fffff800`03699e50 00000000`00000000 : 00000000`00000000 fffffa80`04b741f0 fffffa60`00c0b299 00000000`00000000 : 0xfffffa80`045e0001
STACK_COMMAND: kb
FOLLOWUP_IP:
NETIO!NetioDereferenceNetBufferListChain+137
fffffa60`00b438e7 4c8bb42480000000 mov r14,qword ptr [rsp+80h]
SYMBOL_STACK_INDEX: a
SYMBOL_NAME: NETIO!NetioDereferenceNetBufferListChain+137
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: NETIO
IMAGE_NAME: NETIO.SYS
DEBUG_FLR_IMAGE_TIMESTAMP: 49e02e06
FAILURE_BUCKET_ID: X64_0x19_20_NETIO!NetioDereferenceNetBufferListChain+137
BUCKET_ID: X64_0x19_20_NETIO!NetioDereferenceNetBufferListChain+137
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\DMP\Mini042411-02.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6002 (Service Pack 2) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 6002.18160.amd64fre.vistasp2_gdr.091208-0542
Machine Name:
Kernel base = 0xfffff800`02404000 PsLoadedModuleList = 0xfffff800`025c8dd0
Debug session time: Sun Apr 24 18:50:23.944 2011 (UTC - 4:00)
System Uptime: 0 days 0:06:25.850
Loading Kernel Symbols
...............................................................
................................................................
.......
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {2f, 2, 1, fffff80002468492}
Unable to load image \SystemRoot\System32\drivers\tcpip.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for tcpip.sys
*** ERROR: Module load completed but symbols could not be loaded for tcpip.sys
Probably caused by : afd.sys ( afd!AfdTLFastDgramSendComplete+50 )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 000000000000002f, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80002468492, address which referenced memory
Debugging Details:
------------------
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff8000262b080
000000000000002f
CURRENT_IRQL: 2
FAULTING_IP:
nt!KeAcquireInStackQueuedSpinLock+22
fffff800`02468492 488711 xchg rdx,qword ptr [rcx]
CUSTOMER_CRASH_COUNT: 2
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: hl2.exe
TRAP_FRAME: fffffa600335bbc0 -- (.trap 0xfffffa600335bbc0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000002 rbx=0000000000000000 rcx=000000000000002f
rdx=fffffa600335bd80 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002468492 rsp=fffffa600335bd58 rbp=fffffa800533ef30
r8=fffffa600335bd80 r9=fffffa80046f7780 r10=00000000000000f4
r11=fffffa600335bf68 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz ac pe cy
nt!KeAcquireInStackQueuedSpinLock+0x22:
fffff800`02468492 488711 xchg rdx,qword ptr [rcx] ds:0010:00000000`0000002f=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff8000245e1ee to fffff8000245e450
STACK_TEXT:
fffffa60`0335ba78 fffff800`0245e1ee : 00000000`0000000a 00000000`0000002f 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffffa60`0335ba80 fffff800`0245d0cb : 00000000`00000001 00000000`00000002 fffffa80`046f7780 ffffffff`ffffffff : nt!KiBugCheckDispatch+0x6e
fffffa60`0335bbc0 fffff800`02468492 : fffffa60`03040a40 fffffa80`001c0c92 fffff800`02518647 fffffa60`0335ddb0 : nt!KiPageFault+0x20b
fffffa60`0335bd58 fffffa60`03040a40 : fffffa80`001c0c92 fffff800`02518647 fffffa60`0335ddb0 fffff800`02518647 : nt!KeAcquireInStackQueuedSpinLock+0x22
fffffa60`0335bd60 fffffa60`00e37510 : 00000000`00000000 00000000`00000000 00000000`00000010 00000000`00000202 : afd!AfdTLFastDgramSendComplete+0x50
fffffa60`0335bdb0 00000000`00000000 : 00000000`00000000 00000000`00000010 00000000`00000202 fffffa60`0335bde8 : tcpip+0x31510
STACK_COMMAND: kb
FOLLOWUP_IP:
afd!AfdTLFastDgramSendComplete+50
fffffa60`03040a40 29737c sub dword ptr [rbx+7Ch],esi
SYMBOL_STACK_INDEX: 4
SYMBOL_NAME: afd!AfdTLFastDgramSendComplete+50
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: afd
IMAGE_NAME: afd.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 49e02e35
FAILURE_BUCKET_ID: X64_0xA_afd!AfdTLFastDgramSendComplete+50
BUCKET_ID: X64_0xA_afd!AfdTLFastDgramSendComplete+50
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\DMP\Mini042511-02.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6002 (Service Pack 2) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 6002.18160.amd64fre.vistasp2_gdr.091208-0542
Machine Name:
Kernel base = 0xfffff800`02461000 PsLoadedModuleList = 0xfffff800`02625dd0
Debug session time: Mon Apr 25 03:39:59.884 2011 (UTC - 4:00)
System Uptime: 0 days 2:13:50.211
Loading Kernel Symbols
...............................................................
................................................................
.......
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 19, {20, fffffa8002c093b0, fffffa8002c09520, 4179800}
Unable to load image \SystemRoot\System32\drivers\tcpip.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for tcpip.sys
*** ERROR: Module load completed but symbols could not be loaded for tcpip.sys
Unable to load image \SystemRoot\system32\DRIVERS\Rtlh64.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for Rtlh64.sys
*** ERROR: Module load completed but symbols could not be loaded for Rtlh64.sys
Probably caused by : NETIO.SYS ( NETIO!NetioDereferenceNetBufferListChain+137 )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 0000000000000020, a pool block header size is corrupt.
Arg2: fffffa8002c093b0, The pool entry we were looking for within the page.
Arg3: fffffa8002c09520, The next pool entry.
Arg4: 0000000004179800, (reserved)
Debugging Details:
------------------
BUGCHECK_STR: 0x19_20
POOL_ADDRESS: GetPointerFromAddress: unable to read from fffff80002688080
fffffa8002c093b0
CUSTOMER_CRASH_COUNT: 2
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
PROCESS_NAME: PMB.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff8000259446a to fffff800024bb450
STACK_TEXT:
fffffa60`01722af8 fffff800`0259446a : 00000000`00000019 00000000`00000020 fffffa80`02c093b0 fffffa80`02c09520 : nt!KeBugCheckEx
fffffa60`01722b00 fffffa60`00e8890f : 00000000`ffffff6a fffffa80`5a6f6d74 fffffa80`044caf00 fffffa60`7ffffa80 : nt!ExDeferredFreePool+0x9e3
fffffa60`01722bb0 00000000`ffffff6a : fffffa80`5a6f6d74 fffffa80`044caf00 fffffa60`7ffffa80 00000000`00000001 : tcpip+0x7990f
fffffa60`01722bb8 fffffa80`5a6f6d74 : fffffa80`044caf00 fffffa60`7ffffa80 00000000`00000001 fffffa80`02c091f0 : 0xffffff6a
fffffa60`01722bc0 fffffa80`044caf00 : fffffa60`7ffffa80 00000000`00000001 fffffa80`02c091f0 fffffa80`044c41a0 : 0xfffffa80`5a6f6d74
fffffa60`01722bc8 fffffa60`7ffffa80 : 00000000`00000001 fffffa80`02c091f0 fffffa80`044c41a0 fffffa60`00b418e7 : 0xfffffa80`044caf00
fffffa60`01722bd0 00000000`00000001 : fffffa80`02c091f0 fffffa80`044c41a0 fffffa60`00b418e7 fffffa80`04a6bc40 : 0xfffffa60`7ffffa80
fffffa60`01722bd8 fffffa80`02c091f0 : fffffa80`044c41a0 fffffa60`00b418e7 fffffa80`04a6bc40 00000000`00000001 : 0x1
fffffa60`01722be0 fffffa80`044c41a0 : fffffa60`00b418e7 fffffa80`04a6bc40 00000000`00000001 00000000`00000001 : 0xfffffa80`02c091f0
fffffa60`01722be8 fffffa60`00b418e7 : fffffa80`04a6bc40 00000000`00000001 00000000`00000001 fffffa60`0293d0d5 : 0xfffffa80`044c41a0
fffffa60`01722bf0 fffffa60`00e766dc : fffffa60`01722c78 00000000`00000001 fffffa80`044ca1a0 fffffa80`04d20010 : NETIO!NetioDereferenceNetBufferListChain+0x137
fffffa60`01722cb0 fffffa60`01722c78 : 00000000`00000001 fffffa80`044ca1a0 fffffa80`04d20010 fffffa80`04a6b6d0 : tcpip+0x676dc
fffffa60`01722cb8 00000000`00000001 : fffffa80`044ca1a0 fffffa80`04d20010 fffffa80`04a6b6d0 fffffa60`00c11299 : 0xfffffa60`01722c78
fffffa60`01722cc0 fffffa80`044ca1a0 : fffffa80`04d20010 fffffa80`04a6b6d0 fffffa60`00c11299 fffffa80`044ca050 : 0x1
fffffa60`01722cc8 fffffa80`04d20010 : fffffa80`04a6b6d0 fffffa60`00c11299 fffffa80`044ca050 00000000`00000000 : 0xfffffa80`044ca1a0
fffffa60`01722cd0 fffffa80`04a6b6d0 : fffffa60`00c11299 fffffa80`044ca050 00000000`00000000 00000000`00000000 : 0xfffffa80`04d20010
fffffa60`01722cd8 fffffa60`00c11299 : fffffa80`044ca050 00000000`00000000 00000000`00000000 fffffa80`045b8960 : 0xfffffa80`04a6b6d0
fffffa60`01722ce0 fffffa60`030ee8f0 : 00000000`00000000 fffffa80`044c41a0 fffffa80`04a68010 fffffa80`05a2a010 : ndis!NdisFSendNetBufferListsComplete+0xc9
fffffa60`01722d50 fffffa60`00db324c : fffffa80`044c41a0 fffffa60`00c67110 00000000`00000001 fffffa60`029503bf : pacer!PcFilterSendNetBufferListsComplete+0xf4
fffffa60`01722dc0 fffffa60`0299466d : fffffa80`044c41a0 fffffa80`02c091f0 fffffa80`0459c4a0 fffffa80`044caf00 : ndis!NdisMSendNetBufferListsComplete+0x7c
fffffa60`01722e00 fffffa80`044c41a0 : fffffa80`02c091f0 fffffa80`0459c4a0 fffffa80`044caf00 fffffa80`01e634d0 : Rtlh64+0x766d
fffffa60`01722e08 fffffa80`02c091f0 : fffffa80`0459c4a0 fffffa80`044caf00 fffffa80`01e634d0 fffffa80`044ff028 : 0xfffffa80`044c41a0
fffffa60`01722e10 fffffa80`0459c4a0 : fffffa80`044caf00 fffffa80`01e634d0 fffffa80`044ff028 fffffa80`044c41a0 : 0xfffffa80`02c091f0
fffffa60`01722e18 fffffa80`044caf00 : fffffa80`01e634d0 fffffa80`044ff028 fffffa80`044c41a0 00000000`00000000 : 0xfffffa80`0459c4a0
fffffa60`01722e20 fffffa80`01e634d0 : fffffa80`044ff028 fffffa80`044c41a0 00000000`00000000 00000000`00000000 : 0xfffffa80`044caf00
fffffa60`01722e28 fffffa80`044ff028 : fffffa80`044c41a0 00000000`00000000 00000000`00000000 fffffa80`02b2e4b0 : 0xfffffa80`01e634d0
fffffa60`01722e30 fffffa80`044c41a0 : 00000000`00000000 00000000`00000000 fffffa80`02b2e4b0 00000000`00000000 : 0xfffffa80`044ff028
fffffa60`01722e38 00000000`00000000 : 00000000`00000000 fffffa80`02b2e4b0 00000000`00000000 fffffa60`03c75ca0 : 0xfffffa80`044c41a0
STACK_COMMAND: kb
FOLLOWUP_IP:
NETIO!NetioDereferenceNetBufferListChain+137
fffffa60`00b418e7 4c8bb42480000000 mov r14,qword ptr [rsp+80h]
SYMBOL_STACK_INDEX: a
SYMBOL_NAME: NETIO!NetioDereferenceNetBufferListChain+137
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: NETIO
IMAGE_NAME: NETIO.SYS
DEBUG_FLR_IMAGE_TIMESTAMP: 49e02e06
FAILURE_BUCKET_ID: X64_0x19_20_NETIO!NetioDereferenceNetBufferListChain+137
BUCKET_ID: X64_0x19_20_NETIO!NetioDereferenceNetBufferListChain+137
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\DMP\Mini042611-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6002 (Service Pack 2) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 6002.18160.amd64fre.vistasp2_gdr.091208-0542
Machine Name:
Kernel base = 0xfffff800`02414000 PsLoadedModuleList = 0xfffff800`025d8dd0
Debug session time: Tue Apr 26 08:34:18.504 2011 (UTC - 4:00)
System Uptime: 1 days 4:53:00.248
Loading Kernel Symbols
...............................................................
................................................................
........
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 19, {20, fffffa800551bf20, fffffa800551c380, 44660e0}
Unable to load image \SystemRoot\System32\drivers\tcpip.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for tcpip.sys
*** ERROR: Module load completed but symbols could not be loaded for tcpip.sys
Unable to load image \SystemRoot\system32\DRIVERS\atikmdag.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for atikmdag.sys
*** ERROR: Module load completed but symbols could not be loaded for atikmdag.sys
Unable to load image \SystemRoot\system32\DRIVERS\Rtlh64.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for Rtlh64.sys
*** ERROR: Module load completed but symbols could not be loaded for Rtlh64.sys
Probably caused by : NETIO.SYS ( NETIO!NetioDereferenceNetBufferListChain+137 )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
BAD_POOL_HEADER (19)
The pool is already corrupt at the time of the current request.
This may or may not be due to the caller.
The internal pool links must be walked to figure out a possible cause of
the problem, and then special pool applied to the suspect tags or the driver
verifier to a suspect driver.
Arguments:
Arg1: 0000000000000020, a pool block header size is corrupt.
Arg2: fffffa800551bf20, The pool entry we were looking for within the page.
Arg3: fffffa800551c380, The next pool entry.
Arg4: 00000000044660e0, (reserved)
Debugging Details:
------------------
BUGCHECK_STR: 0x19_20
POOL_ADDRESS: GetPointerFromAddress: unable to read from fffff8000263b080
fffffa800551bf20
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
PROCESS_NAME: hl2.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff8000254746a to fffff8000246e450
STACK_TEXT:
fffffa60`01722af8 fffff800`0254746a : 00000000`00000019 00000000`00000020 fffffa80`0551bf20 fffffa80`0551c380 : nt!KeBugCheckEx
fffffa60`01722b00 fffffa60`00e8390f : 00000000`ffffff6a fffffa80`5a6f6d74 fffffa80`044c7f00 fffffa60`7ffffa80 : nt!ExDeferredFreePool+0x9e3
fffffa60`01722bb0 00000000`ffffff6a : fffffa80`5a6f6d74 fffffa80`044c7f00 fffffa60`7ffffa80 00000000`00000001 : tcpip+0x7990f
fffffa60`01722bb8 fffffa80`5a6f6d74 : fffffa80`044c7f00 fffffa60`7ffffa80 00000000`00000001 fffffa80`0551bd60 : 0xffffff6a
fffffa60`01722bc0 fffffa80`044c7f00 : fffffa60`7ffffa80 00000000`00000001 fffffa80`0551bd60 fffffa80`044bd1a0 : 0xfffffa80`5a6f6d74
fffffa60`01722bc8 fffffa60`7ffffa80 : 00000000`00000001 fffffa80`0551bd60 fffffa80`044bd1a0 fffffa60`00b428e7 : 0xfffffa80`044c7f00
fffffa60`01722bd0 00000000`00000001 : fffffa80`0551bd60 fffffa80`044bd1a0 fffffa60`00b428e7 fffffa80`04ab3110 : 0xfffffa60`7ffffa80
fffffa60`01722bd8 fffffa80`0551bd60 : fffffa80`044bd1a0 fffffa60`00b428e7 fffffa80`04ab3110 00000000`00000001 : 0x1
fffffa60`01722be0 fffffa80`044bd1a0 : fffffa60`00b428e7 fffffa80`04ab3110 00000000`00000001 00000000`00000001 : 0xfffffa80`0551bd60
fffffa60`01722be8 fffffa60`00b428e7 : fffffa80`04ab3110 00000000`00000001 00000000`00000001 fffffa60`022f04c1 : 0xfffffa80`044bd1a0
fffffa60`01722bf0 fffffa60`00e716dc : fffffa60`01722c01 fffffa60`022eed01 fffffa60`01722cf4 fffffa80`04ba5180 : NETIO!NetioDereferenceNetBufferListChain+0x137
fffffa60`01722cb0 fffffa60`01722c01 : fffffa60`022eed01 fffffa60`01722cf4 fffffa80`04ba5180 fffffa80`04b226f0 : tcpip+0x676dc
fffffa60`01722cb8 fffffa60`022eed01 : fffffa60`01722cf4 fffffa80`04ba5180 fffffa80`04b226f0 fffffa60`00c0a299 : 0xfffffa60`01722c01
fffffa60`01722cc0 fffffa60`01722cf4 : fffffa80`04ba5180 fffffa80`04b226f0 fffffa60`00c0a299 fffffa80`02b9b5b0 : atikmdag+0xe1d01
fffffa60`01722cc8 fffffa80`04ba5180 : fffffa80`04b226f0 fffffa60`00c0a299 fffffa80`02b9b5b0 fffff800`0247705a : 0xfffffa60`01722cf4
fffffa60`01722cd0 fffffa80`04b226f0 : fffffa60`00c0a299 fffffa80`02b9b5b0 fffff800`0247705a 00000000`0000008d : 0xfffffa80`04ba5180
fffffa60`01722cd8 fffffa60`00c0a299 : fffffa80`02b9b5b0 fffff800`0247705a 00000000`0000008d fffffa60`005ec9d0 : 0xfffffa80`04b226f0
fffffa60`01722ce0 fffffa60`030fa8f0 : 00000000`00000000 fffffa80`044bd1a0 fffffa80`04ab6010 fffffa60`01722d80 : ndis!NdisFSendNetBufferListsComplete+0xc9
fffffa60`01722d50 fffffa60`00dac24c : fffffa80`044bd1a0 fffffa60`00c60110 00000000`00000001 fffffa60`022f0035 : pacer!PcFilterSendNetBufferListsComplete+0xf4
fffffa60`01722dc0 fffffa60`02d5f66d : fffffa80`044bd1a0 fffffa80`0551bd60 fffffa80`04542cc0 fffffa80`0450b000 : ndis!NdisMSendNetBufferListsComplete+0x7c
fffffa60`01722e00 fffffa80`044bd1a0 : fffffa80`0551bd60 fffffa80`04542cc0 fffffa80`0450b000 fffffa80`01e78890 : Rtlh64+0x766d
fffffa60`01722e08 fffffa80`0551bd60 : fffffa80`04542cc0 fffffa80`0450b000 fffffa80`01e78890 fffffa80`0450b028 : 0xfffffa80`044bd1a0
fffffa60`01722e10 fffffa80`04542cc0 : fffffa80`0450b000 fffffa80`01e78890 fffffa80`0450b028 fffffa80`044bd1a0 : 0xfffffa80`0551bd60
fffffa60`01722e18 fffffa80`0450b000 : fffffa80`01e78890 fffffa80`0450b028 fffffa80`044bd1a0 00000000`00000000 : 0xfffffa80`04542cc0
fffffa60`01722e20 fffffa80`01e78890 : fffffa80`0450b028 fffffa80`044bd1a0 00000000`00000000 00000000`00000000 : 0xfffffa80`0450b000
fffffa60`01722e28 fffffa80`0450b028 : fffffa80`044bd1a0 00000000`00000000 00000000`00000000 fffffa80`04598780 : 0xfffffa80`01e78890
fffffa60`01722e30 fffffa80`044bd1a0 : 00000000`00000000 00000000`00000000 fffffa80`04598780 00000000`00000000 : 0xfffffa80`0450b028
fffffa60`01722e38 00000000`00000000 : 00000000`00000000 fffffa80`04598780 00000000`00000000 fffffa60`09c82ca0 : 0xfffffa80`044bd1a0
STACK_COMMAND: kb
FOLLOWUP_IP:
NETIO!NetioDereferenceNetBufferListChain+137
fffffa60`00b428e7 4c8bb42480000000 mov r14,qword ptr [rsp+80h]
SYMBOL_STACK_INDEX: a
SYMBOL_NAME: NETIO!NetioDereferenceNetBufferListChain+137
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: NETIO
IMAGE_NAME: NETIO.SYS
DEBUG_FLR_IMAGE_TIMESTAMP: 49e02e06
FAILURE_BUCKET_ID: X64_0x19_20_NETIO!NetioDereferenceNetBufferListChain+137
BUCKET_ID: X64_0x19_20_NETIO!NetioDereferenceNetBufferListChain+137
Followup: MachineOwner
---------
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [F:\DMP\Mini042711-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows Server 2008/Windows Vista Kernel Version 6002 (Service Pack 2) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 6002.18160.amd64fre.vistasp2_gdr.091208-0542
Machine Name:
Kernel base = 0xfffff800`02463000 PsLoadedModuleList = 0xfffff800`02627dd0
Debug session time: Tue Apr 26 22:46:52.180 2011 (UTC - 4:00)
System Uptime: 0 days 2:32:31.570
Loading Kernel Symbols
...............................................................
................................................................
........
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 3B, {c0000005, fffffa600300d40a, fffffa60059f1be0, 0}
Probably caused by : afd.sys ( afd!AfdTLReleaseIndications+1a )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: fffffa600300d40a, Address of the instruction which caused the bugcheck
Arg3: fffffa60059f1be0, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
FAULTING_IP:
afd!AfdTLReleaseIndications+1a
fffffa60`0300d40a 488b4108 mov rax,qword ptr [rcx+8]
CONTEXT: fffffa60059f1be0 -- (.cxr 0xfffffa60059f1be0)
rax=fffffa600300f4e0 rbx=00000000ffffffff rcx=0000000000000000
rdx=fffffa60059f2460 rsi=fffffa8001f0b4e0 rdi=fffffa8004ee4250
rip=fffffa600300d40a rsp=fffffa60059f2440 rbp=fffffa60059f2ca0
r8=0000000000000000 r9=0000000000000001 r10=0000000000000000
r11=00000000045cfa14 r12=fffffa8001e72010 r13=fffffa60059f2a98
r14=0000000000000000 r15=fffffa60059f2790
iopl=0 nv up ei ng nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010282
afd!AfdTLReleaseIndications+0x1a:
fffffa60`0300d40a 488b4108 mov rax,qword ptr [rcx+8] ds:002b:00000000`00000008=????????????????
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x3B
PROCESS_NAME: PMB.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from fffffa6003040fa6 to fffffa600300d40a
STACK_TEXT:
fffffa60`059f2440 fffffa60`03040fa6 : fffffa60`059f2970 00000000`ffffffff fffffa80`04cf2570 00000000`00000000 : afd!AfdTLReleaseIndications+0x1a
fffffa60`059f2490 fffffa60`0302efe1 : fffffa80`01e72010 fffffa60`059f2790 fffffa60`00000400 fffffa80`04ee4250 : afd!AfdFastConnectionReceive+0x517
fffffa60`059f26b0 fffff800`0271facc : 00000000`00000400 fffffa60`0302e010 fffffa80`01ee57a0 fffffa80`0203b001 : afd!AfdFastIoDeviceControl+0xfd1
fffffa60`059f2a10 fffff800`027287a6 : fffffa60`059f2ba8 00000000`0000030c 00000000`00000001 00000000`00000000 : nt!IopXxxControlFile+0x34c
fffffa60`059f2b40 fffff800`024bcef3 : 00000000`00000000 0000001e`82538d46 00000000`00000000 fffff800`024b5cd6 : nt!NtDeviceIoControlFile+0x56
fffffa60`059f2bb0 00000000`74da385e : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`043ae908 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x74da385e
FOLLOWUP_IP:
afd!AfdTLReleaseIndications+1a
fffffa60`0300d40a 488b4108 mov rax,qword ptr [rcx+8]
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: afd!AfdTLReleaseIndications+1a
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: afd
IMAGE_NAME: afd.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 49e02e35
STACK_COMMAND: .cxr 0xfffffa60059f1be0 ; kb
FAILURE_BUCKET_ID: X64_0x3B_afd!AfdTLReleaseIndications+1a
BUCKET_ID: X64_0x3B_afd!AfdTLReleaseIndications+1a
Followup: MachineOwner
---------